Table of Contents
Introduction
Choosing the right open source router OS is crucial for home, enterprise, and cloud data center networks. Using free open source router OS solutions can reduce costs while providing flexibility and extensive feature extensions, allowing users to deploy networks according to different scenarios.
This article categorizes the discussion into three scenarios: enterprise/cloud data centers (AsterNOS-VPP , VyOS), small to medium-sized enterprises (pfSense, OPNsense, IPFire), and home use (OpenWrt, DD-WRT).
To provide readers with a clear understanding of the advantages, disadvantages, and applicable scenarios of different open-source Router OS, this article presents comparison tables and concrete examples. Whether you are a home user, IT administrator, or data center engineer, this information can serve as a practical reference.
Ⅰ. Enterprise / Cloud Data Center Open-Source Router OS (AsterNOS-VPP, VyOS)
These two open source router OS solutions offer key features such as high-performance routing, automation, and support for BGP, EVPN, and MPLS. They are designed to meet the needs of service providers and cloud data centers, targeting large enterprises, ISPs, and cloud computing data centers.
1. AsterNOS-VPP
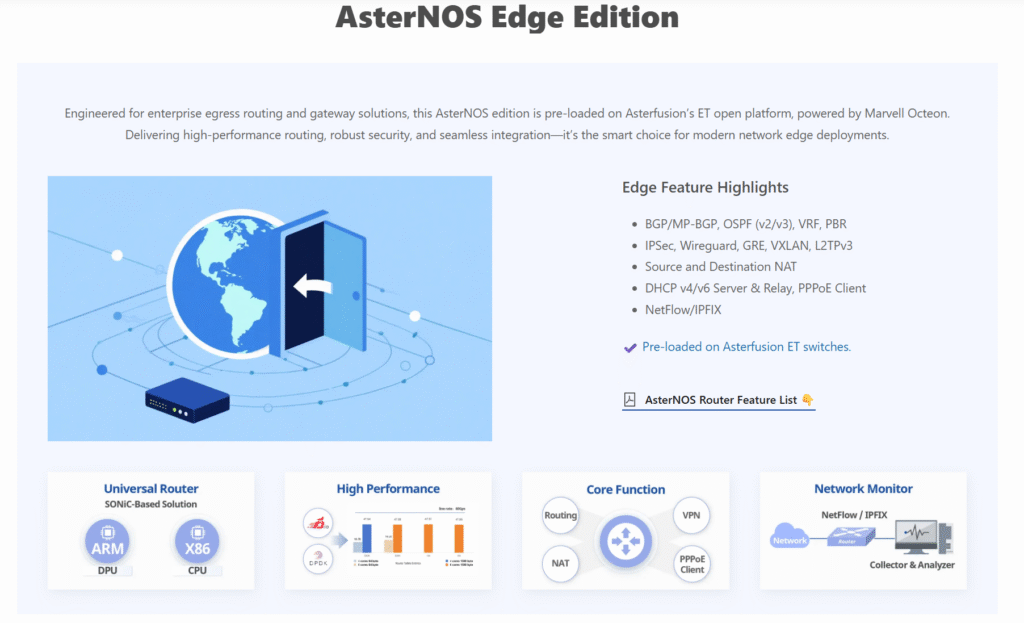
AsterNOS-VPP is a network operating system developed by Asterfusion based on the SONiC ecosystem and Linux. It integrates the SONiC control plane with a high-performance VPP data plane, converting SAI commands into VPP API calls to achieve high-speed data forwarding on DPU/CPU. It runs on ARM (such as Marvell OCTEON series), x86, and virtualization platforms (KVM, VMware ESXi), supporting deployments from small and medium enterprises to large data centers.
Its core advantage lies in integration with VPP/DPDK, accelerating data plane forwarding.
Functionally, AsterNOS-VPP is similar to VyOS but more focused on data center and enterprise networks. It supports BGP/OSPF, IPsec/WireGuard VPN, RADIUS authentication, multi-WAN policies, mesh network traffic scheduling, and line-rate L3 routing, NAT/CGNAT.
It is highly customizable, supporting RESTful API, gNMI/NetConf integration with automation platforms such as Ansible and OpenStack. Users can define custom routing and firewall policies, and extend features like NetFlow and IPS through plugins without changing hardware to meet evolving business needs.
The operation mode combines Web interface and Klish CLI. Basic configurations like DHCP, routing, and VPN can be quickly completed. Inheriting SONiC’s ZTP functionality, new devices can automatically load configurations. Core enterprise features, including VLAN, QoS, and PPPoE, are natively integrated. Advanced users can implement complex setups such as high availability, dual-stack IPv4/IPv6, and traffic mirroring through scripts or APIs.
Limitations include a high entry barrier for beginners. Complex operations, such as full BGP optimization, VPP parameter tuning, or automation scripts, require understanding the SONiC ecosystem and network principles. While core functions (routing, basic VPN, firewall) work on white-box switches, achieving peak performance depends on DPU (e.g., Marvell OCTEON) or switches supporting DPDK(e.g., ET2508 or ET3608-2P2S).
Please refer to the AsterNOS Router Version Datasheet for more details.
Notably, click on the AsterNOS-VPP image to download the NOS and Quick Start Guide, and experiment with the system yourself.
2. VyOS

VyOS is developed based on Linux and originated from Vyatta in 2013. It targets small and medium enterprises, research institutions, and edge computing scenarios, and runs reliably on x86_64 industrial PCs, servers, virtual machines (VMware, KVM), and some ARM devices.
Compared with pfSense, OPNsense, and IPFire, VyOS’s main advantage is stronger enterprise-level routing capabilities. It supports static routing, RIP, OSPF, and BGP, making it suitable for multi-branch interconnections. Built-in IPsec, OpenVPN, and WireGuard ensure secure remote access.
VyOS is highly customizable, supporting the installation of network monitoring, traffic analysis, and log storage tools via package management. It can also integrate with automation platforms through APIs for batch deployment. For specialized network requirements, kernel parameters can be modified or routing algorithms customized to adapt to non-standard network scenarios.
Operation relies primarily on the CLI, with the Web interface as a supplement. The CLI supports command completion and configuration rollback, suitable for IT personnel with network knowledge to perform complex configurations. The Web interface provides basic configuration and status monitoring. Core enterprise features, such as VLAN, QoS, and port aggregation, are deeply integrated and support interface mapping in virtualized environments, covering everything from basic connectivity to complex network setups.
The drawbacks include a high barrier to entry for beginners, as CLI usage requires understanding command structure. Support for niche hardware drivers is limited, and the Web interface is basic; complex operations still rely on CLI, making it less user-friendly for those expecting a graphical interface.
3. Why VyOS and AsterNOS-VPP Are Suitable for Enterprise/Cloud Data Centers
1. Open source and Linux-based
VyOS is an open-source network operating system based on Debian and is a community fork of Vyatta, licensed under GPL. AsterNOS-VPP is built on the SONiC kernel, which is also open source. Being Linux-based and open-source, both offer advantages such as customizability and strong community support.
2. Powerful network capabilities
They support multiple routing protocols, including BGP, OSPF, and IS-IS, enabling efficient routing management and network interconnection. Both provide robust firewall, NAT, and VPN features to meet enterprise security and connectivity requirements. AsterNOS-VPP leverages DPDK/VPP toolkits to accelerate traffic forwarding.
3. High reliability
They support VRRP (Virtual Router Redundancy Protocol), WAN load balancing, and connection state synchronization, ensuring high availability and stability while reducing the risk of network downtime in enterprise environments.
Both AsterNOS-VPP and VyOS exemplify robust open source router OS solutions suitable for high-performance and scalable enterprise or cloud networks. Organizations seeking free open source router OS can leverage these systems to build reliable and customizable infrastructures.
Ⅱ. SME-Focused Open-Source Router OS (pfSense / OPNsense / IPFire)
All three open source router OS focus on comprehensive firewall, VPN, and security features, targeting small and medium-sized enterprises (SMEs), educational institutions, and branch offices.
1. pfSense
pfSense is developed based on the FreeBSD system (not Linux, but also a Unix-like system) and supports functionality extension via third-party free packages. Originally derived from the m0n0wall firmware in 2004, its goal was to provide a stable open-source routing firewall. Over the years, pfSense has become a benchmark in the open-source firewall field, capable of running stably on x86-based industrial PCs, servers, and some dedicated hardware.
In terms of software features, pfSense comes with many enterprise-level capabilities, such as IPsec VPN, NAT, and port forwarding, all configurable through an intuitive web interface without requiring UNIX knowledge or command-line operations. Using CARP (Common Address Redundancy Protocol), it can also provide high availability through failover. For advanced needs, users can extend functionality through the package system, including IDS/IPS (Snort, Suricata), WireGuard VPN, and advanced client management. pfSense also supports cloud deployment and can be directly purchased from the AWS or Azure Marketplace.
Regarding hardware, pfSense is software-only; users can choose hardware as needed, including Netgate desktop or rack devices, or self-selected white-box or virtualized hardware.
Overall, pfSense still has a learning curve for beginners. While basic network configuration is relatively simple, advanced tasks such as failover setup, dynamic routing protocols, or IDS/IPS rule optimization require network knowledge and consultation of official documentation or community tutorials. Although hardware compatibility is broad, multi-port industrial PCs or older devices may need manual NIC matching, making initial setup slightly more challenging compared with commercial firewalls.
In practice, pfSense has been adopted by many SMEs and ISPs. For example, an ISP in Bangladesh deployed a security gateway combining pfSense with FRR, effectively blocking most malware and spyware, significantly reducing customer complaints, while the core devices required fewer restarts.
2. OPNsense
OPNsense is also developed based on the FreeBSD system (another Unix-like system) and inherits the core features of open-source firewalls. It was forked from pfSense in 2014 and, like pfSense, organizes its functionality into “built-in features + plugin extensions.”
In terms of usability, OPNsense offers a more modern and visual web interface compared with pfSense, including setup wizards and a “beginner mode,” making it easier for IT personnel with limited experience to complete basic security configurations quickly. Similar to pfSense, it supports firewall, NAT/port forwarding, and authentication features—such as WPA2-Enterprise and RADIUS—through a web interface without requiring command-line operations. Advanced features, such as IDS/IPS policies, detailed rule management, traffic analysis, and network monitoring, require plugin extensions.
Regarding hardware, OPNsense is software-only; users can select their preferred hardware, including white-box systems, virtual machines, or dedicated firewall appliances.
However, there is still a learning curve for beginners. While basic security configuration is guided, advanced operations—such as tuning IDS/IPS rules or configuring failover parameters—require an understanding of network security principles and reference to official tutorials or community examples. Additionally, some advanced plugins (e.g., specialized encryption modules) require manual installation of dependencies. Compared with commercial devices that come pre-installed, plugin configuration can be more demanding, and very low-end or older hardware (e.g., with less than 2GB RAM) may experience performance issues.
3. IPFire
Unlike the previous two, IPFire is developed on Linux and is widely applicable. Originally designed as a “lightweight, efficient open-source firewall,” IPFire has become the preferred choice for small and medium-sized enterprises with simple network setups, thanks to its lightweight design and modular architecture. It can run smoothly on low-end x86 industrial PCs or older servers, requiring very little hardware resources.
IPFire focuses on three aspects: lightweight, modularity, and ease of use.
Lightweight means that although the features are divided into “built-in + plugin extensions,” the built-in functions are minimal, covering the most common needs such as basic firewall, NAT, VPN (OpenVPN/IPsec), basic VLAN, QoS, and simple authentication. Advanced features, like IDS/IPS, traffic monitoring, and advanced VPN client management, are implemented through additional components or scripts.
Modular means only the needed functions are enabled, avoiding redundancy.
Ease of use is reflected in the simple web interface, with visual configuration for core functions. Only essential features, such as DHCP setup, firewall rules, and VPN management, are displayed. Beginners can quickly find what they need and even complete “internet access + basic firewall” setup without prior learning.
Hardware efficiency comes from the lightweight, modular design and streamlined system services, allowing IPFire to run on low-end servers, industrial PCs, or even virtual machines.
Limitations include that IPFire is less suitable for complex enterprise scenarios. It lacks high-availability features like failover and BGP, making it unsuitable for multi-branch high-availability deployments. Wireless support depends on specific network cards and requires additional AP configuration, so network flexibility is lower than commercial devices.
According to AWS Marketplace user feedback, IPFire scores 10 out of 10 for stability during use, and being free makes it extremely cost-effective.
In summary, among these three open-source router OS, compared with pfSense, OPNsense focuses more on security and ease of use, while IPFire is lighter and better suited for small businesses with limited hardware resources. All three are suitable for small to medium-sized enterprises, branch offices, or networks with tight budgets.
4. Why pfSense, OPNsense, and IPFire Are Suitable for SMEs
1. Cost Control
No license fees and support for standard hardware greatly reduce entry barriers
Small and medium-sized enterprises (SMEs) are often budget-conscious. These three systems are open-source and free, requiring only hardware costs, unlike enterprise firewalls from vendors like Cisco or Huawei that charge high annual license fees, often ranging from thousands to tens of thousands of dollars. They also support standard x86 hardware, such as regular industrial PCs or repurposed old servers, and can even be built from scratch using “CPU + NIC + memory.”
2. Precise Functionality
Covering over 90% of core network needs for SMEs
SMEs typically do not require complex features like SDN (Software-Defined Networking) or multi-region clustering, but they have clear needs for security, stable connectivity, and bandwidth management. These three systems natively meet such requirements. For example, basic connectivity is supported through static routing, dynamic routing (RIP/OSPF), DHCP servers, and DNS caching to ensure stable internal network operations.
3. Low Technical Threshold
All three provide web-based visual management interfaces with clear logic for core functions such as VPN configuration and firewall rules. Even IT teams with limited experience can quickly start maintenance using official documentation and active community support.
pfSense, OPNsense, and IPFire are leading open source router OS for SMEs, providing secure, stable, and cost-effective solutions. Businesses seeking free open source router OS can deploy them on standard hardware without expensive licenses.
Ⅲ. Home Use Open-Source Router OS (OpenWrt, DD-WRT)
Both of these open source router OS are easy to flash, have large communities, and support a wide range of hardware. They are designed for home broadband users, tech enthusiasts, and small SOHO setups.
1. OpenWrt
OpenWrt is a Linux-based open source router OS firmware designed for embedded devices, primarily to enable network traffic routing on such devices. A key feature is its writable file system and package management system, which allows users to customize any router with over 27,000 available software packages to meet specific application requirements.
OpenWrt also provides a web-based management interface with high customizability. Users can modify the software to implement specific network functions according to their needs. For example, by installing the luci-app-openvpn package, OpenWrt allows configuration of OpenVPN clients or servers via the web GUI, enabling home remote access or branch office VPN setups.
Advanced network configurations are supported, including Quality of Service (QoS), Network Address Translation (NAT), and VLAN tagging.
However, the default interface may not be very beginner-friendly and requires some learning. Additionally, installation and configuration on x86 hardware can be less straightforward compared with OPNsense or pfSense.
2. DD-WRT
DD-WRT is also Linux-based firmware. It was originally developed to unlock the full potential of Linksys’ classic WRT54G router, and has since expanded to support hundreds of router models.
It fully supports RADIUS authentication based on the WPA2 protocol. Additionally, it includes the routing protocols and wireless modes required to build mesh networks, meeting the needs of distributed network deployments.
DD-WRT is highly customizable, allowing modifications ranging from simple interface adjustments to more complex functional enhancements.
It balances ease of use with advanced features. The software comes with a web-based management interface where basic settings, such as changing the WiFi name or password, are simple to configure. While it does not have as many software packages as OpenWrt, core networking tools such as Quality of Service (QoS), Network Address Translation (NAT), and VLAN are built in. Advanced users can further extend functionality using custom scripts (Startup/Shutdown/Firewall scripts), enabling more complex network setups such as VPNs or firewalls.
However, it is not particularly beginner-friendly. While basic operations are simple, using advanced features like VPNs or VLANs requires some learning. Additionally, when flashing firmware on older routers, hardware models must be matched precisely; a wrong choice can render the router unusable. Compared to official firmware with one-click updates, the process has a higher entry barrier.
3. Why OpenWrt and DD-WRT Are Suitable for Home Use
Home routers essentially need to be sufficient, flexible, and low-cost, and OpenWrt and DD-WRT meet these requirements well:
1. Low deployment and hardware requirements
Wide device support: Both open source router OS firmware projects are mainly designed for consumer-grade routers and can run on most models available in the market.
Simple deployment: Installation only requires flashing the firmware, without the need for dedicated servers or high-performance hardware.
2. High Compatibility for Multi-Device Connectivity
Home networks include a wide variety of devices—such as smartphones, computers, and gaming consoles—and some devices have specific requirements for network protocols (like IPv6, Mesh, 802.11ac/ax) or features (such as port aggregation and UPnP). Both OpenWrt and DD-WRT have active communities where users can access information on hardware compatibility, firmware installation guides, configuration instructions, and how to extend functionality.
Within the OpenWrt community, for example, users can find guidance on enabling IPv6 on older routers or setting up a low-cost mesh network using multiple routers with 802.11s or WireGuard.
Both open source router OS firmware options offer extensive extensibility: OpenWrt allows additional features through plugins, such as ad blocking, traffic monitoring, and NAS functionality. DD-WRT includes most core network tools by default, and users can further enhance performance and security through the web interface or custom scripts to manage Wi-Fi signal, QoS, and VPN clients.
3. Low Learning and Management Overhead
DD-WRT’s WebUI is relatively simple and intuitive, while OpenWrt’s LuCI interface has gradually improved, making configuration easier for users. Most home network setups involve only Wi-Fi, bandwidth allocation, and basic VPN, so there’s no need to understand advanced protocols like BGP, EVPN, or MPLS. Users without professional networking knowledge can quickly get started.
Overall, OpenWrt and DD-WRT are popular examples of open source routing software, offering flexibility and cost efficiency for home users. Those looking for free open source router OS solutions will find them ideal for low-cost mesh networks and VPN setups.
Finally, this table compares the key features of popular open source router OS for enterprise, SME, and home users.
| Category | Software | Core Features | Advanced Features | Usability | Hardware Requirements | Typical Use Case |
| Enterprise / Data Center | AsterNOS-VPP | High-speed data plane forwarding (VPP/DPDK), multi-WAN policy, mesh traffic scheduling | BGP/OSPF, IPsec/WireGuard VPN, RADIUS auth, HA, dual-stack IPv4/IPv6, traffic mirroring | Web UI + Klish CLI, ZTP auto-configuration | ARM (Marvell OCTEON), x86, virtualization platforms | Data centers, cloud computing, high-throughput enterprise networks, automated operations |
| Enterprise / Data Center | VyOS | Enterprise routing, multi-branch connectivity, VPN, API automation | Static routing, RIP, OSPF, BGP, IPsec/OpenVPN/WireGuard, traffic monitoring, logging | CLI-based, Web UI secondary, advanced operations require network knowledge | x86_64 industrial PCs, servers, VMs, some ARM devices | Enterprise routing, multi-branch interconnect, remote access, security management |
| SME | pfSense | Enterprise-level firewall, VPN, CARP high availability | IDS/IPS, dynamic routing, client management | Web UI intuitive, basic easy, advanced requires networking knowledge | x86 industrial PCs, servers, dedicated hardware | SMB firewall, VPN, stable connectivity |
| SME | OPNsense | High security, modern Web UI, plugin-based | IDS/IPS, advanced rule management, traffic monitoring | Wizard and beginner mode, highly usable | Whitebox, virtual machines, dedicated firewall | SMB firewall, VPN, security management |
| SME | IPFire | Lightweight, modular, low resource consumption | Basic firewall, NAT, VPN, VLAN, QoS, IDS/IPS via add-ons | Clean Web UI, core functions visualized | x86 low-end industrial PCs, old servers, virtual machines | Small business, low-cost network protection |
| Home | OpenWrt | Writable filesystem, 27,000+ packages, highly customizable, Web GUI | QoS, NAT, VLAN, VPN client/server | Web UI usable, but beginners need learning | Consumer routers/embedded devices | Home networks, low-cost Mesh, remote access |
| Home | DD-WRT | Core networking tools built-in, Web UI + custom scripts | QoS, NAT, VLAN, VPN, firewall, Mesh networking | Basic operations simple, advanced features require learning | Consumer routers, strict hardware matching | Home networks, low-cost Mesh, advanced configuration |
Conclusion
In my view, for a typical office or home environment, OpenWrt, DD-WRT, or pfSense/OPNsense/IPFire are solid choices. For cloud or AI scenarios, where throughput and latency are critical, AsterNOS-VPP or VyOS are more suitable. Additionally, AsterNOS-VPP receives quarterly updates, ensuring it stays current with performance and security enhancements.
Of course, categorizing open-source router OS by “home / small business / enterprise/data center” is just a convenient way to understand and compare them, not a strict boundary. In reality, any open source router OS has potential for various applications—the difference lies in their “default use case” and “development threshold.” All of these options are open source router OS, providing users the freedom to customize features, but it ultimately depends on whether your team has the capability to do so.



