Build Next-Gen High-Performance IPsec Gateway by AsterNOS VPP & Hardware Offload
written by Asterfuison
Table of Contents
Introduction
In the wave of digital transformation, enterprise network boundaries are expanding rapidly. As fiber optic broadband evolves toward 10G, 25G, and even 100G, network engineers face a thorny challenge: How to build High-Performance IPsec Gateway and achieve security encryption performance that matches bandwidth capabilities within an open network architecture?
Traditional software routing solutions often fall short when facing massive volumes of encrypted traffic. Today, we will delve into the technical logic behind this bottleneck and deconstruct how AsterNOS utilizes VPP Vector Packet Processing and Hardware Offload technology to shatter the performance ceiling.
Before delving into how AsterNOS-VPP achieves high-performance IPsec gateway functionality, it’s important to understand what IPsec is, how it works, and its application scenarios.
What is IPsec?
IPsec (Internet Protocol Security) defined by the IETF is a suite of open standards at the IP layer that adds security to any IP traffic, regardless of the application or protocol above it.
Its main goals are:
- Confidentiality: Encrypt IP packets so that eavesdroppers cannot understand the content (e.g., when running enterprise traffic over the public network).
- Integrity: Ensure that the packets are not tampered with during transmission (to prevent man-in-the-middle attacks).
- Authentication: Verify the identity of the peer to confirm “I am truly communicating with the correct gateway or host,” preventing spoofing/deception.
- Anti-replay: Prevent attackers from capturing packets and re-sending old ones (using sequence numbers and window mechanisms to discard replayed packets).
Since it operates at the network layer, IPsec provides “underlying encryption” for any IP-based application and can also be used to establish VPN tunnels (such as site-to-site or remote-access), creating a logical “dedicated channel” over the public network.
Core Components of IPsec
In this “security framework,” IPsec is primarily composed of three core components:
- AH (Authentication Header): Provides data origin authentication and integrity validation to ensure packets have not been tampered with, but does not provide encryption.
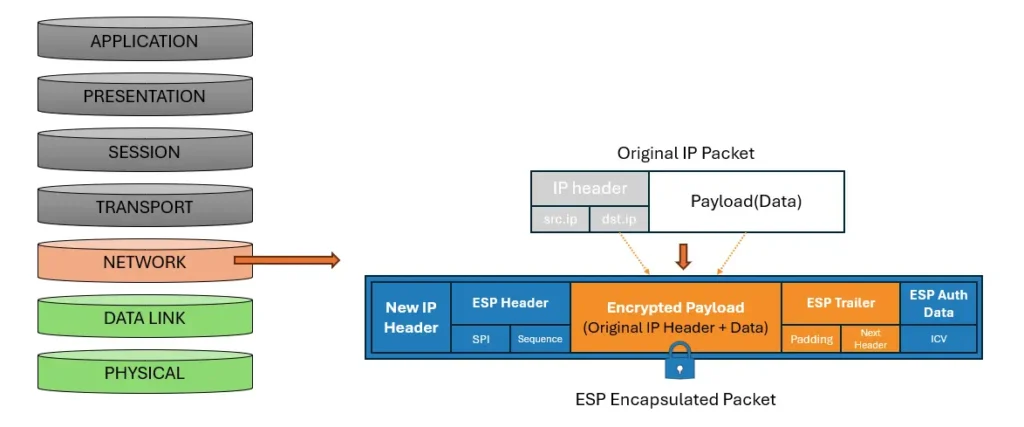
- ESP (Encapsulating Security Payload): Provides encryption, authentication, and integrity validation. This is the most performance-intensive part of VPNs as it requires encrypting the data payload. ESP alone covers most scenarios since it combines features, whereas AH is rarely used standalone due to its lack of confidentiality.
- IKE (Internet Key Exchange): Used for automatically negotiating keys and establishing Security Associations (SAs).
How does IPsec Work?
IPsec operates at the network layer (Layer 3) to intercept and process traffic. Its working modes are primarily divided into two types:
Encapsulation Mode: Tunnel vs. Transport
- Tunnel Mode: This is the most commonly used mode for inter-enterprise connections. The entire original IP packet is encapsulated within a new IP header. It hides the internal network’s real IP addresses and is typically used for gateway-to-gateway (Site-to-Site) connections.
- Transport Mode: Only the payload of the original IP packet is encrypted, while the original IP header remains unchanged. This mode is typically used for end-to-end communication between two hosts.
IPsec Communication Workflow
1. Traffic Steering (Interest Flow Matching): AsterNOS adopts a Virtual Tunnel Interface (VTI, originally proposed by Cisco) architecture that aligns with cloud-native networking concepts. The IPsec tunnel is treated as a standard logical Layer 3 interface. Traffic entry into the tunnel is controlled by the routing table, simplifying complex policy configurations.
2. IKE Negotiation (Control Plane): Both parties establish a secure channel and negotiate specific keys and algorithms.
3. Data Transmission (Data Plane): The sender uses the SA to perform ESP encapsulation on the original IP packet (encrypting the payload and adding headers), while the receiver decrypts and validates the ICV (Integrity Check Value).
IPsec Gateway Deployment Scenarios
Site-to-Site VPN
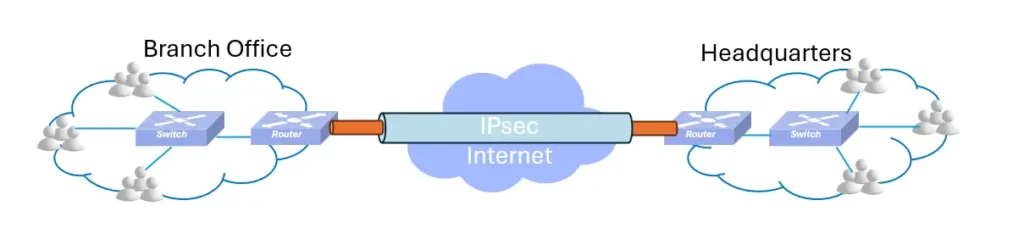
The most typical scenario is interconnecting enterprise branch offices (Site-to-Site VPN). Assume the Headquarters network (192.168.1.0/24) needs to communicate with a Branch network (10.1.1.0/24). By deploying IPsec gateways at both headquarters and branch offices, we establish a virtual encrypted tunnel over the untrusted public network (Internet). All data flowing through this tunnel is automatically encrypted before leaving the gateway and decrypted upon entry, remaining transparent to end-users.
Scalable Architecture: Hub-and-Spoke VPN (Multi-Site)
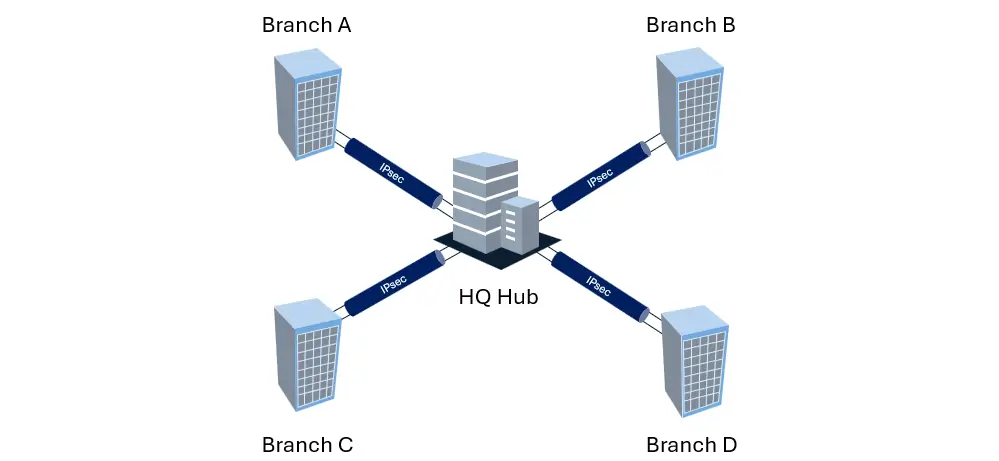
In a site-to-site scenario, for enterprises with centralized management needs, a Hub-and-Spoke topology is the standard for efficiency. In this scenario, the Headquarters IPsec gateway acts as a central Hub, aggregating concurrent secure tunnels from multiple distributed Branch offices. AsterNOS leverages its high-performance forwarding plane to handle these concentrated encryption loads without bottlenecks, allowing enterprises to easily scale from a few branches to hundreds while maintaining a simplified, unified security policy.
Other Topology Type in IPsec
One of the most common topologies in enterprise wide-area networks is the Hub-and-Spoke (Star) architecture. With proper redundancy design, this architecture strikes a good balance between reliability, link cost, and management complexity, which is why it was emphasized in the previous discussion.
For special scenarios with extremely high requirements for latency and path control, such as financial transactions or real-time communication, some systems adopt a Full-Mesh topology to achieve direct interconnection between critical sites. Alternatively, a hybrid mode is used (where key core sites are directly connected, and regular edge sites are routed through the hub). However, these two modes are generally associated with higher link bandwidth costs and increased routing and operational complexity. They are typically used in specific high-demand scenarios and are less versatile, so this article will not delve further into these topics.
Remote-Access VPN
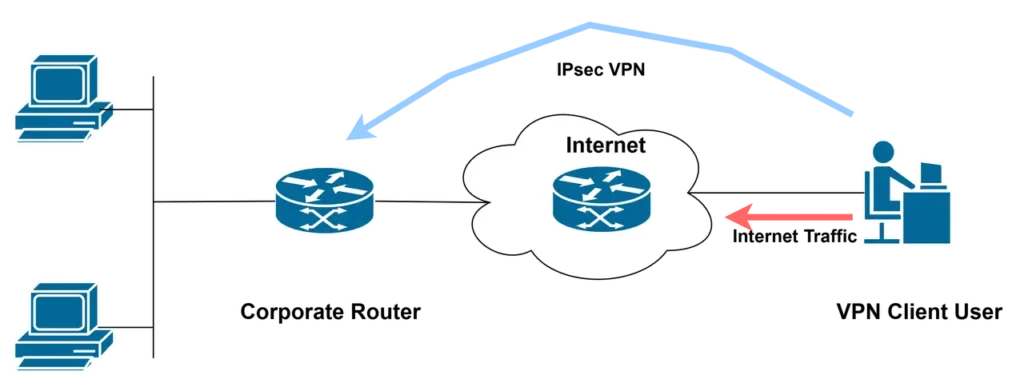
Employees working from home or on business trips can securely access the company’s internal network through an IPsec client installed on their devices. This is achieved via a high-strength encrypted tunnel and strict authentication mechanisms. This not only ensures the confidentiality and integrity of the transmitted data, but also allows smooth access to internal resources (such as file servers, OA systems, internal databases, etc.). This mode effectively extends the enterprise security perimeter, perfectly adapting to flexible working and remote collaboration scenarios, while ensuring business continuity under compliance.
Host-to-Host VPN
Deploying IPsec in transport mode between two servers enables host-level, end-to-end network layer encryption. This solution is suitable for high-security scenarios where public IPs are reachable, such as core financial transactions and government confidential systems. In transport mode, only the data payload is encrypted, while the original IP header is retained. It requires the IP addresses of both communicating parties to be routable within the network, ensuring efficient end-to-end protection.
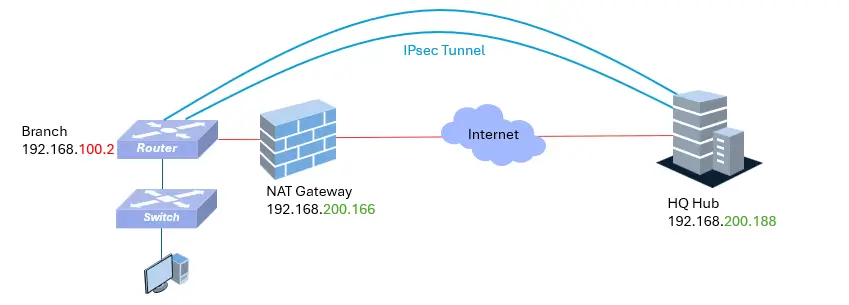
NAT Traversal (NAT-T): Overcoming Network Boundaries
Real-world network deployments are often complex, with branch gateways frequently deployed behind ISP modems or firewalls (NAT) without public IP addresses. AsterNOS addresses this challenge with built-in NAT Traversal (NAT-T) capabilities. This allows the IPsec gateway to encapsulate encrypted traffic to penetrate intermediate NAT devices, preventing the ESP protocol (50) from being dropped by NAT devices, and ensuring it can correctly identify itself to the Headquarters.
Having understood the basics of IPsec, we now need to explore how enterprise SONiC AsterNOS-VPP goes beyond traditional CPU-based IPsec processing when building an IPsec gateway.
Performance Bottleneck of Traditional IPsec Gateway on Legacy CPUs
In traditional network architectures, the general-purpose CPU (x86/ARM) is the core processor. While CPUs excel at handling complex control logic, they have inherent disadvantages when handling compute-intensive ESP encapsulation tasks.
Every data packet passing through the interface requires high-intensity mathematical operations (AES encryption/decryption) and SHA hash verification.
- Context Switching Overhead: Under high-concurrency traffic of 10Gbps+, the massive volume of packets leads to frequent CPU interrupts and context switching, consuming a significant amount of computing resources.
- Control Plane Instability: When the CPU is saturated by encryption tasks, keepalive packets for routing protocols (BGP/OSPF) may be delayed, leading to network instability.
This mismatch of “using general-purpose compute for specialized tasks” leads to a precipitous drop in throughput and a sharp increase in latency.
How VPP-based Enterprise SONiC Boosts IPsec Gateway Performance
How AsterNOS-VPP Solves the Traditional IPsec Bottleneck
To thoroughly resolve the performance bottleneck, AsterNOS did not simply do “addition” but conducted a complete reconstruction of the underlying architecture. We provide a dual acceleration scheme where “software sets the baseline, and hardware breaks the ceiling.”
- First Evolution: The Software Architecture Revolution Even without specialized hardware acceleration cards, AsterNOS outperforms traditional routing. Traditional Linux IPsec processing operates as a “packet-by-packet interrupt” process, which is highly inefficient. In contrast, AsterNOS is based on the VPP (Vector Packet Processing) architecture, which processes packets in “batches.” This is akin to the difference in efficiency between a bus (transporting dozens of people at once) and a taxi (transporting one person at a time). This allows AsterNOS to achieve IPsec processing performance far superior to traditional Linux kernels, even when using only general-purpose CPUs.
- Second Evolution: Unleashing Hardware Capabilities (Hardware Offload) When bandwidth demands rise to 10G/25G+ line rates, we introduce IPsec Hardware Offload. By incorporating a dedicated Crypto Engine, we completely offload the heavy mathematical calculations from the CPU. The CPU is responsible only for “issuing commands,” while the hardware handles the “brute force calculations.”
Actual Control Plane and Data Plane Processing of IPsec
AsterNOS constructs a full-link acceleration architecture combining SONiC Control Plane + VPP Vectorized Forwarding + Hardware Offload, offering flexible choices for businesses of different scales.
The architectural design of AsterNOS ingeniously achieves the decoupling of the control plane and the data plane:
- Control Plane (SONiC Containerized Management): AsterNOS adopts a database-driven control plane. User configuration intent is first written into the Configuration Database (Config_DB), validated and converted by the intelligent management process (ipsecmgrd), and then issued to the underlying Hardware Abstraction Layer Database (ASIC_DB). Additionally, the IKE service process responsible for key negotiation runs on the general-purpose CPU. It handles complex identity authentication and key exchange logic; once negotiation is complete, it pushes the generated Security Association (SA) to the data plane.
- Data Plane Path A: VPP Vectorized Software Acceleration (General Scenario): On standard servers, VPP utilizes unique Vector Batching technology to ensure key processing code always resides in the CPU’s L1 Instruction Cache (I-cache). It handles ESP encapsulation and decryption entirely in user space, avoiding the latency caused by frequent memory reads in the traditional Linux kernel.
- Data Plane Path B: DPDK Zero-Copy Hardware Offload (Extreme Scenario): This is the key to performance acceleration. VPP communicates directly with the underlying hardware acceleration unit (Crypto VF) via the DPDK Cryptodev interface. Data packets are read, encrypted/decrypted, and have their ICV calculated directly by the hardware engine without repeated copying in memory, and are subsequently sent directly to the physical interface.
Benefits of AsterNOS-VPP Architecture
Based on laboratory test data, this architecture (Control Plane + VPP Vectorized Forwarding + Hardware Offload) brings significant advantages:
- Software-Defined Flexibility: Even on devices without hardware acceleration cards, AsterNOS provides an excellent performance baseline via the VPP software architecture, sufficient for the VPN needs of most SMEs.
- Near-Physical Line-Rate Throughput: In a 4x10GE physical network setup, AsterNOS easily achieved an aggregated encryption throughput of 35.2 Gbps with 512-byte packet. This figure has reached the bandwidth limit of the current physical interfaces (rather than the limit of the encryption engine).
- Extremely Low CPU Usage: With heavy encryption calculations offloaded, the CPU focuses on business logic and policy control, no longer becoming a bottleneck.
- Broad Algorithm Compatibility: Comprehensive support for efficient AES-GCM (128/192/256) algorithms, while compatible with AES-CBC/CTR. It supports DH groups up to MODP-8192 and ECP-521, meeting financial-grade security compliance requirements.
Conclusion: The Future of High-Performance Enterprise Interconnection
For a long time, when planning security gateways, enterprise networks have had to face a difficult trade-off: choose general-purpose software routing with high flexibility but limited performance, or choose dedicated hardware that is powerful but closed and expensive?
AsterNOS offers a third answer through a heterogeneous computing architecture.
By deeply fusing VPP’s vectorized software efficiency with DPDK Hardware Offload’s deterministic computing power, AsterNOS successfully decouples the control plane from the data plane. This architectural innovation not only allows standard hardware to unleash line-rate encryption capabilities comparable to dedicated ASICs but also preserves the openness and programmability of the SONiC cloud-native ecosystem.
For enterprises moving towards the 10Gbps+ interconnection era, this means you no longer need to pay an expensive “performance tax” for encryption. AsterNOS is dedicated to making high-performance IPsec gateway a default infrastructure capability, empowering enterprises to build next-generation interconnected networks that are more agile, secure, and cost-effective.
Want to experience it firsthand?
Please refer to our accompanying document, IPsec-VPP Case, for detailed configuration steps and verification methods.
Contact US !
- To request a proposal, send an E-Mail to bd@cloudswit.ch
- To receive timely and relevant information from Asterfusion, sign up at AsterNOS Community Portal
- To submit a case, visit Support Portal
- To find user manuals for a specific command or scenario, access AsterNOS Documentation
- To find a product or product family, visit Asterfusion-cloudswit.ch




