OAuth 2.0 for OpenWiFi Controller: Securing Asterfusion Network Platform
written by Asterfuison
Table of Contents
Introduction
If you have followed Asterfusion’s recent updates, you may have noticed significant improvements in the login mechanism of the TIP-based Open WiFi Controller, specifically the introduction of OAuth 2.0.

What does OAuth 2.0 for openWiFi controller mean? It means you can log in to our OpenWiFi controller using GitHub, Google, Microsoft, or Feishu to perform operations. This method does not require exposing your password, nor do you need to contact us to create an account. It enables direct use of the controller for a quick experience, without going through a complicated account registration process.
So how does Asterfusion implement OAuth 2.0 for OpenWiFi controller?
Ⅰ. Role of Asterfusion OpenWiFi Controller
In today’s digital era, network connectivity has evolved from simple “wireless access” to “ubiquitous interconnection.” OpenWiFi, as an open wireless network ecosystem, promotes standardization and scalability for enterprise networks.
The Asterfusion OpenWiFi Controller is built on the TIP OpenWiFi standard, but it is not limited to wireless management. It is a cloud-native unified network control platform capable of managing both wired and wireless devices. This enables end-to-end visibility and centralized control from access points (APs) and switches to routers.
In practical deployments, the Asterfusion Controller can not only connect to standard OpenWiFi APs but also work collaboratively with enterprise wired devices, achieving configuration synchronization, unified policies, and network automation. By upgrading to the OpenWiFi Plus software package, the controller can further expand compatibility, supporting unified management of multi-vendor AP devices, providing enterprises with greater flexibility and operational efficiency under an open network architecture.
Want to know more about the OpenWiFi Controller? Please visit Asterfusion launches TIP-based OpenWiFi Network Controller
Ⅱ. Why OAuth 2.0 for openwifi controller Matters
Limitations of Traditional Username/Password Authentication
In multi-vendor, multi-tenant enterprise networks, traditional username/password authentication increasingly fails to meet requirements. Consider a typical work environment: the production system uses one set of credentials, the employee system uses another, and enterprises may require passwords to be unique and complex. This creates a need to remember multiple accounts and passwords. In network operations, passwords often need to be changed regularly for security, adding further burden on employees.
Overall, traditional authentication shows clear shortcomings in usability, operational cost, and security.
Advantages of OAuth 2.0
In the context of OAuth 2.0 for OpenWiFi Controller, the following benefits demonstrate why token-based access is a better approach.
Token-based, password-free access: OAuth 2.0 defines four core roles: Resource Owner, Client, Authorization Server, and Resource Server. When a user (Resource Owner) logs into a client, they are redirected to the Authorization Server. After successful authorization, the server issues an Access Token to the client. The client accesses the Resource Server using the token instead of the user’s password, reducing risks in password transmission and storage. Tokens typically have short lifetimes, limiting potential misuse.
Seamless integration with third-party IdPs: OAuth 2.0 can integrate with existing identity providers (IdPs) such as Google, Azure AD, or Okta. Users can log in with existing accounts, and enterprises can leverage their identity directories for unified management, reducing duplicate accounts and operational overhead.
Fine-grained permissions and lifecycle control: Using scopes, short-lived Access Tokens, and Refresh Tokens, applications can control resource access and manage token validity. In case of compromise, access can be revoked or limited, while automatic refresh maintains user experience.
Extension: Brief Overview of OpenID Connect
OpenID Connect (OIDC) is a standard built on OAuth 2.0 that adds user authentication. Why is it needed? OAuth 2.0 handles authorization—confirming whether a user has permission to access a resource—but does not verify “who” the user is. Modern systems often require knowing the user’s identity. OIDC addresses this by adding an ID Token (usually a signed JWT) to the OAuth flow, which proves the user’s identity to the client. The ID Token contains basic user information such as username, email, and user ID. By verifying the ID Token, the system can authenticate the user while maintaining secure authorization.
In the Asterfusion OpenWiFi Controller, OAuth 2.0 combined with OpenID Connect enables both secure cross-system authorization and unified user identity management and login experience.
Ⅲ. Asterfusion’s OAuth 2.0 for OpenWiFi Controller Implementation
Compliance with Standards and Security Mechanisms
The Asterfusion OpenWiFi Controller strictly adheres to the OAuth 2.0 standard, employing a secure and standardized Authorization Code Flow with Proof Key for Code Exchange (PKCE) throughout the authentication and authorization process to ensure user data security.
During client and authorization server interactions, the controller follows the exact request and response format defined by OAuth 2.0. When the client requests authorization, it sends parameters such as client_id, redirect_uri, and response_type to the authorization server. After verifying the client’s identity and request parameters, the authorization server returns an authorization code or an Access Token.
To further protect login credentials, the OpenWiFi Controller implements the PKCE mechanism to secure the authorization code. When initiating an authorization request, the client generates a pair of temporary keys—code_verifier and code_challenge. The authorization server validates the request by hashing the code_verifier to obtain a new code_challenge and comparing it to the original one. Only when they match is an access token issued. This process effectively prevents interception, substitution, or replay attacks, enhancing both security and data integrity.
This architecture ensures that OAuth 2.0 for OpenWiFi Controller aligns with modern zero-trust authentication principles.
For token generation and validation, the Asterfusion OpenWiFi Controller applies robust encryption and signing mechanisms to ensure token security and validity, preventing forgery or tampering. (The implementation supports multiple algorithms—no single algorithm is mandated.)
Supported Identity Providers (IdPs)
The Asterfusion OpenWiFi Controller supports multiple mainstream identity providers (IdPs), including Google, GitHub, Microsoft, and Feishu.
Taking Google integration as an example, the administrator only needs to enter the client_id and client_secret provided by Google in the controller’s configuration interface to establish communication and authorization with Google’s identity authentication server. Through this integration, users can log in directly with their existing Google accounts, without registering a separate account. This ensures secure access while improving the overall login experience.
Through these integrations, OAuth 2.0 for OpenWiFi Controller delivers seamless login experiences across multiple identity systems.
User Authorization Flow
The entire authorization process follows the OAuth 2.0 + PKCE standard and can be summarized in the following steps:
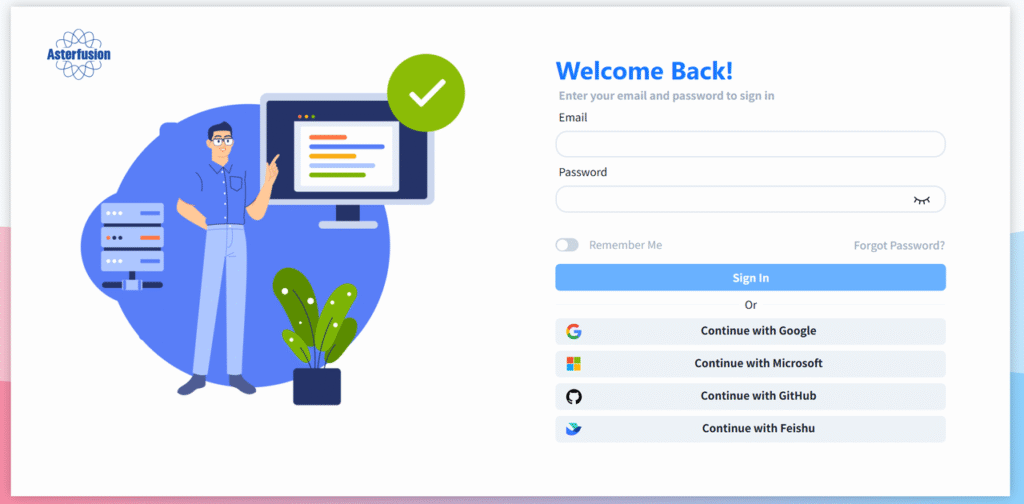
- 1. The user selects “Continue with [IdP]” on the login page, such as “Continue with Google.”
- 2. The browser redirects the user to the corresponding identity provider’s authorization page, for example, the Google login page.
- 3. The user reviews and confirms the authorization request.
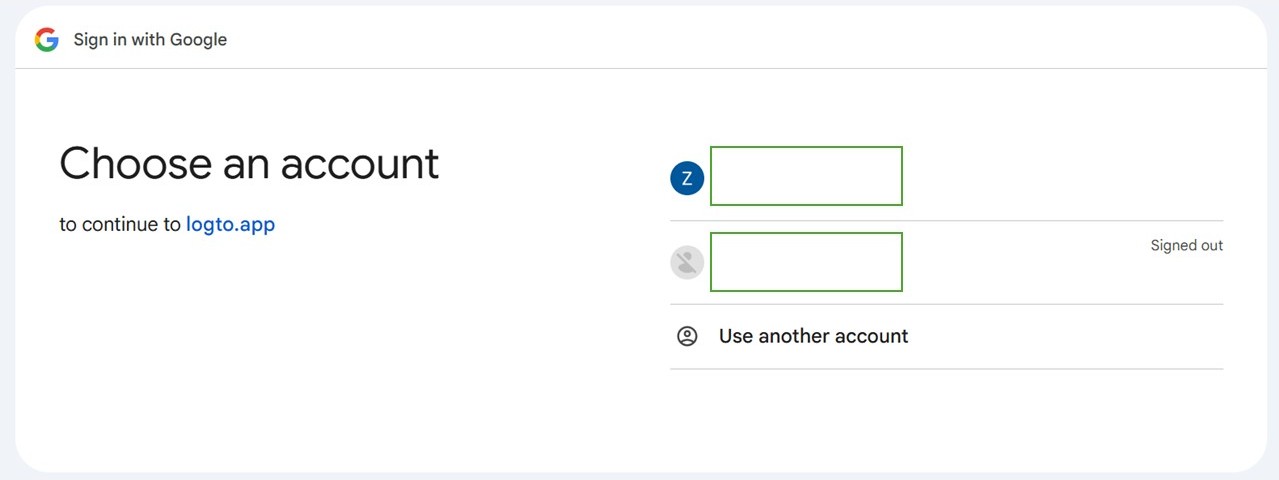
- 4. After verifying the user’s identity, the identity provider generates an Authorization Code and returns it to the Asterfusion OpenWiFi Controller through a redirect request to the specified redirect_uri.
- 5. The Controller receives the authorization code and sends a request to the authorization server for an access token, including parameters such as client_id, client_secret, and code_verifier.
- 6. The authorization server validates the request and verifies the code_verifier. Once confirmed, it issues an Access Token and a Refresh Token.
- 7. After verifying the token’s validity, the Controller grants the user access to protected resources.
When logging in with Feishu, users receive an authorization notification directly within the Feishu app, adding an extra layer of account security — similar to the verification flow used with Microsoft accounts.
Token Lifecycle and Security Policies
Managing the lifecycle of access tokens is a key component of the security framework in OAuth 2.0 for OpenWiFi Controller.
The Asterfusion OpenWiFi Controller typically assigns a short validity period to access tokens. Even if a token is accidentally exposed, an attacker can only use it for a very limited time, thereby reducing potential risks.
When an access token expires, the controller uses a Refresh Token to request a new access token from the authorization server. The refresh token has a longer lifespan but is securely stored in the server-side database with encryption to prevent unauthorized access. In practice, this means users do not need to repeat the authentication process frequently.
During token transmission, all requests are sent over HTTPS encrypted channels to prevent interception or tampering. The controller also performs strict validation on each received token, verifying its signature, issuer, validity period, and permission scope to ensure that only legitimate and valid tokens can access protected resources.
Ⅳ. Security and Operational Benefits
OAuth 2.0 for OpenWiFi Controller not only strengthens access security but also simplifies enterprise network management workflows.
Security Benefits
- Reduced Risk of Password Exposure: OAuth 2.0 eliminates the need to enter or transmit usernames and passwords during login. When you log in using a third-party account, your original credentials are never shared at any stage of the authorization process. Instead, the system uses a token issued by the authorization server to access resources. The entire process is conducted over an HTTPS-encrypted channel, significantly reducing the risk of password leakage.
- Protection Against Multiple Attack Vectors: As mentioned earlier, tokens are protected during transmission through HTTPS, making decryption nearly impossible even if intercepted. This effectively mitigates the risk of man-in-the-middle attacks. Moreover, OAuth 2.0 enhances phishing resistance by requiring users to complete authorization through official login pages (e.g., the Google login page) rather than third-party sites, preventing attackers from stealing passwords via spoofed interfaces.
Operational Management Advantages
- Unified Identity Management and Auditing: With OAuth 2.0 integration, the Asterfusion OpenWiFi Controller enables unified identity management. For example, as an administrator, you no longer need to manually create new accounts for team members. They can log in directly using existing corporate Feishu accounts. This approach streamlines onboarding while ensuring that access is automatically revoked when an employee leaves or their account is deactivated, reducing the risk of orphaned accounts and potential security exposure. On the auditing side, OAuth 2.0 supports detailed logging. The authorization server records login times, IP addresses, and granted access scopes. Operations teams can use these records to trace access behavior, detect abnormal logins, and identify unauthorized activities, enhancing overall network security.
- Enterprise IdP Integration: Integrating with an enterprise Identity Provider (IdP) is another major operational advantage of OAuth 2.0. For example, if your organization uses Feishu as its corporate IdP, users can log in to the controller directly with their Feishu credentials—no additional registration required.
- Automatic Token Refresh: The automatic token refresh mechanism greatly improves both user experience and operational efficiency. In OAuth 2.0, access tokens are designed with short lifespans to minimize security risks. Automatic token refresh solves the need for repeated reauthorization—your session remains active as long as you don’t manually log out or clear your cache, providing a seamless login experience.
Overall, OAuth 2.0 for OpenWiFi Controller enhances both network security and operational efficiency across enterprise deployments.
But what’s the real benefit for you ?
Trying out our product is simple and flexible — no need to contact us or go through extra setup.
If you already have a Google, Microsoft, GitHub, or Feishu account, you can log in directly and experience the OpenWiFi Controller demo environment right away.
👉 Try openWiFi Controller — Asteria Campus Controller
💬 Leave your feedback on the AsterNOS Community Portal
Ⅴ. Conclusion
The adoption of OAuth 2.0 for OpenWiFi Controller makes the Asterfusion authentication framework more open, secure, and scalable.
It eliminates the complexity and risks associated with traditional username-password authentication, while allowing enterprises to integrate their existing identity management systems—such as Google Workspace, Microsoft Entra ID, or Feishu—for unified access control and audit management.
In multi-tenant, multi-vendor network environments, this standards-based identity framework enables smoother system integration, more efficient user access, and greater control over permission assignment and revocation.
For administrators, OAuth 2.0 for OpenWiFi Controller provides centralized and transparent user management; for end users, it enables fast and secure access to the controller without additional registration or repeated authorization.
As Asterfusion continues to advance in open networking and cloud-native management, identity authentication based on open protocols will further enhance the balance between security and usability, delivering a more reliable foundation for unified enterprise network management.
FAQs
Some basic concepts about OAuth 2.0:
What is OAuth 2.0, and how is it different from OAuth 1.0?
OAuth 2.0 is an open standard authorization framework that allows applications to access protected resources on behalf of a user—without exposing the user’s password. Compared to OAuth 1.0, OAuth 2.0 is simpler, more flexible, and easier to integrate. It relies entirely on HTTPS to ensure secure transmission, removing the need for request signing. OAuth 2.0 also introduces multiple Authorization Grant types to support different environments such as web, mobile, and IoT.
What are the four roles in OAuth 2.0 (Resource Owner, Client, Authorization Server, Resource Server)?
OAuth 2.0 defines four core roles:
- Resource Server: Hosts protected resources and validates tokens (for example, the controller’s management API).
- Client: The application requesting access to the resource (e.g., the OpenWiFi Controller).
- Authorization Server: Authenticates the user and issues access tokens.
- Resource Server: Hosts protected resources and validates tokens (for example, the controller’s management API).
Is OAuth 2.0 for authentication or authorization?
Strictly speaking, OAuth 2.0 is an authorization framework—it issues tokens to confirm whether a client is allowed to access a resource. If the system also needs to identify who the user is, OpenID Connect (OIDC) is layered on top of OAuth 2.0 to enable authentication (identity verification).
How does the Authorization Code Grant flow work?
The Authorization Code Grant is the most common and secure OAuth 2.0 flow, typically used in web applications. Basic process:
- The user selects an identity provider (IdP) on the client (e.g., OpenWiFi Controller login page) and is redirected to the IdP’s login page.
- After successful login and authorization, the authorization server returns an Authorization Code.
- The client exchanges this code, along with its credentials (client_id, client_secret), for an Access Token.
- The authorization server validates the request and issues an Access Token, which the client uses to access the Resource Server.
To enhance security, modern implementations use PKCE (Proof Key for Code Exchange) to prevent code interception.
OAuth 2.0 defines several authorization grant types, each suited for different client types such as web apps, mobile apps, backend servers, and IoT devices.
OAuth 2.0 defines multiple Authorization Grant types, each suited for different client types.
| Authorization Grant Type | Typical Use Case | User Interaction Required | Recommended |
| Authorization Code Grant | Web applications, mobile apps (exchange token via backend server) | ✅ Yes | ✅ Recommended |
| Authorization Code with PKCE | Mobile apps / Single Page Applications (SPA) | ✅ Yes | ✅ Recommended (modern best practice) |
| Client Credentials Grant | Backend-to-backend communication (no user) | ❌ No | ✅ Recommended |
| Resource Owner Password Credentials (ROPC) | Trusted clients (legacy systems) | ✅ Yes | ❌ Not recommended |
| Implicit Grant | Early frontend-only applications (no backend) | ✅ Yes | 🚫 Deprecated (removed in OAuth 2.1) |
| Device Code Grant | Devices that cannot directly input credentials (e.g., smart TVs, IoT) | ✅ Yes | ✅ Recommended |
| Refresh Token Grant | Used to refresh access tokens | ❌ No | ✅ Recommended |
What does OAuth 2.1 deprecate or change?
OAuth 2.1 is an updated, security-hardened consolidation of OAuth 2.0. It removes risky mechanisms and incorporates best practices, including:
- Deprecation of Implicit Grant and Password Grant due to high security risks and potential token exposure.
- Mandatory PKCE for all authorization code flows to prevent interception.
- Exact redirect_uri matching to block redirect-based attacks.
- Prohibition of access_token in URLs to prevent exposure in browser history or logs.
- Single-use refresh tokens to reduce the risk of token theft.
Why use OAuth 2.0 instead of OAuth 2.1?
OAuth 2.1 has not yet been widely adopted, and most of its improvements are already implemented in modern OAuth 2.0 frameworks. The Asterfusion OpenWiFi Controller uses a secure architecture combining OAuth 2.0 + PKCE + HTTPS, following OAuth 2.1’s key security practices. This approach ensures compatibility with major identity providers such as Google, Microsoft, GitHub, and Feishu while maintaining strong security and reliability.
Contact US !
- To receive timely and relevant information from Asterfusion, sign up at AsterNOS Community Portal
- To submit a case, visit Support Portal.
- To find user manuals for a specific command or scenario, access AsterNOS Documentation
- To find a product or product family, visit Asterfusion-cloudswit.ch .
- To contact Sales, Send E-Mail to bd@cloudswit.ch



