Guarding the Gate: 5 Essential Authentication Protocols for Network Switch
written by Asterfuison
Table of Contents
In today’s enterprise networks, security, access control, and device management are essential to infrastructure design. As switching environments grow more complex, ensuring that only authorized users and devices can access internal resources is a key challenge.Network authentication protocols address this by managing access, enforcing dynamic policies, and integrating with tools like firewalls, NAC, and zero-trust frameworks to enhance security and control. This article introduces five essential network authentication protocols, outlining their definitions, roles in switch networks, and key pros and cons to help you choose the right solution for your needs.
What Is a “Network Authentication Protocol” in a Switch?
A Network Authentication Protocol is a security mechanism implemented at the network access layer. When a terminal device (like a computer, printer, or smartphone) tries to connect to a switch and access network resources, this protocol ensures the user or device is authenticated first. Only those who pass the authentication can officially enter the internal network.
In simple terms: A network authentication protocol is like a gatekeeper or access control system—it checks who you are before letting you into the network.
Why Are Network Authentication Protocols Important?
In a network without authentication, anyone can connect a cable or join Wi-Fi and gain access. This poses serious risks:
Security Risks:
- Malicious actors could connect freely and launch ARP spoofing or sniff sensitive data.
- Internal users might access resources beyond their permissions.
- Unauthorized devices (IoT, personal laptops) could connect, creating unknown vulnerabilities.
Management Challenges:
- No visibility into who’s connected—device management becomes chaotic.
- Users from different departments all end up in the same VLAN, making segmentation impossible.
- Hard to implement dynamic access control aligned with NAC or zero-trust models.
Here’s a summary of 5 common network authentication protocols widely used in switch-based network environments (including access, aggregation, and core switches). Each protocol includes a definition, its specific role in switching scenarios, along with key advantages and disadvantages to help you better understand and compare them.
5 Essential Authentication Protocols for Switch Networks
1. What Is 802.1X Authentication?(Port-Based Network Access Control)
802.1X authentication is a port-based network access control protocol widely used in enterprise networks. It ensures that only authorized devices or users can access the internal network. It is typically applied at the access layer of the network—on network switches or wireless access points.
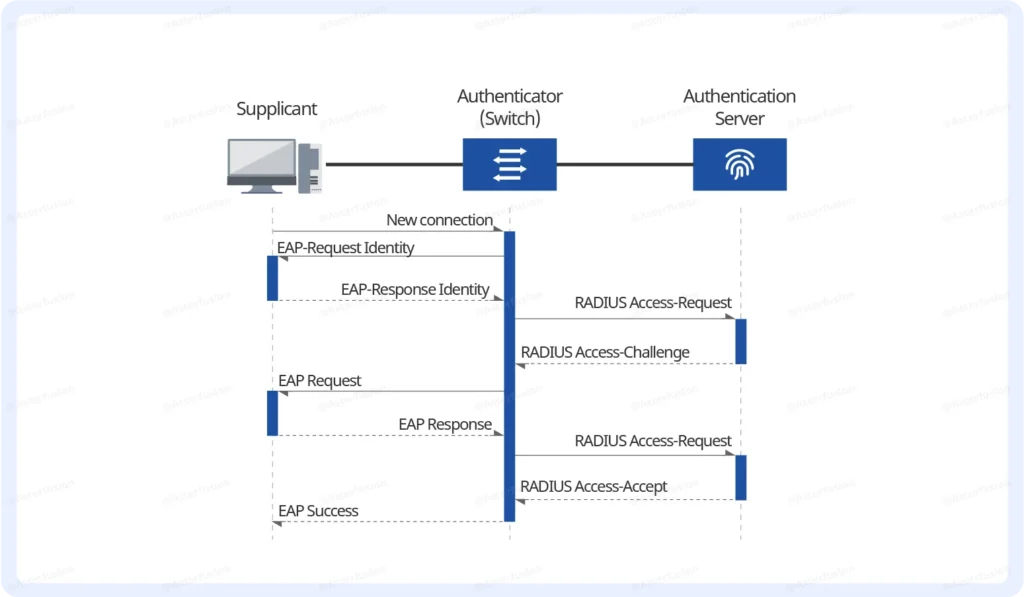
How Does It Work:
- The device connects to the network
The supplicant connects via Ethernet or Wi-Fi and attempts to join the network. - Authenticator blocks traffic and initiates authentication
The switch (authenticator) initially blocks data traffic and begins the 802.1X handshake. - Supplicant sends identity credentials
Using an EAP method (e.g., EAP-TLS or PEAP), the supplicant provides username, password, or a certificate. - Authenticator forwards credentials to the authentication server
The switch encapsulates the EAP messages into a RADIUS request and forwards it to the authentication server. - The authentication server validates the identity
The RADIUS server checks the credentials (e.g., user database, certificate validity). - Access granted or denied
- If the identity is valid, the server sends an “Access-Accept” message, and the switch opens the port for full network access.
- If not, the device is denied access.
2. What is EAP and How Does It Work?
EAP (Extensible Authentication Protocol) is an authentication framework used in network access control. It’s not an authentication method itself but a container protocol that supports various authentication mechanisms between a client and an authentication server.
EAP (Extensible Authentication Protocol) is widely used across various network environments, including wireless networks (such as WPA/WPA2-Enterprise), wired networks (via 802.1X), as well as VPNs and PPP connections. As a flexible authentication framework, it provides secure identity verification for different types of network access.
How EAP Works
EAP typically works in conjunction with 802.1X and involves three main components:
- Supplicant: The client device (e.g., laptop, phone) requesting access
- Authenticator: A network device like a switch or wireless access point that sits between the client and the authentication server
- Authentication Server: Usually a RADIUS server that validates the user’s credentials

Typical Workflow:
[1] Supplicant → Authenticator: Initiates connection
[2] Authenticator → Supplicant: Sends EAP request (e.g., identity)
[3] Supplicant → Authenticator: Sends EAP response (e.g., username)
[4] Authenticator → Server: Forwards EAP data via RADIUS to the authentication server
[5] Server ↔ Supplicant: Exchanges EAP messages to complete authentication (e.g., password/certificate)
[6] Server → Authenticator: Sends authentication success/failure
[7] Authenticator → Supplicant: Grants or denies network access
| Method | Description | Security Level |
|---|---|---|
| EAP-TLS | Certificate-based mutual authentication | Very High |
| EAP-TTLS | TLS tunnel with username/password inside | High |
| PEAP | Similar to EAP-TTLS, developed by Microsoft | High |
| EAP-MD5 | Basic method, vulnerable to attacks, deprecated | Low |
| EAP-SIM/AKA | SIM card-based, used in mobile networks | Medium to High |
3. What Is RADIUS and How Does It Work?
A centralized Authentication, Authorization, and Accounting (AAA) protocol for verifying user or device identities, managing access permissions, and logging network usage.
RADIUS operates as a client-server model involving:
| Component | Role Description |
|---|---|
| RADIUS Client | The end device or user is trying to gain network access. |
| RADIUS Server | Centralized server (e.g., FreeRADIUS, Windows NPS) that handles authentication and policy decisions. |
| User/Supplicant | The end device or user trying to gain network access. |
Step-by-Step Workflow:
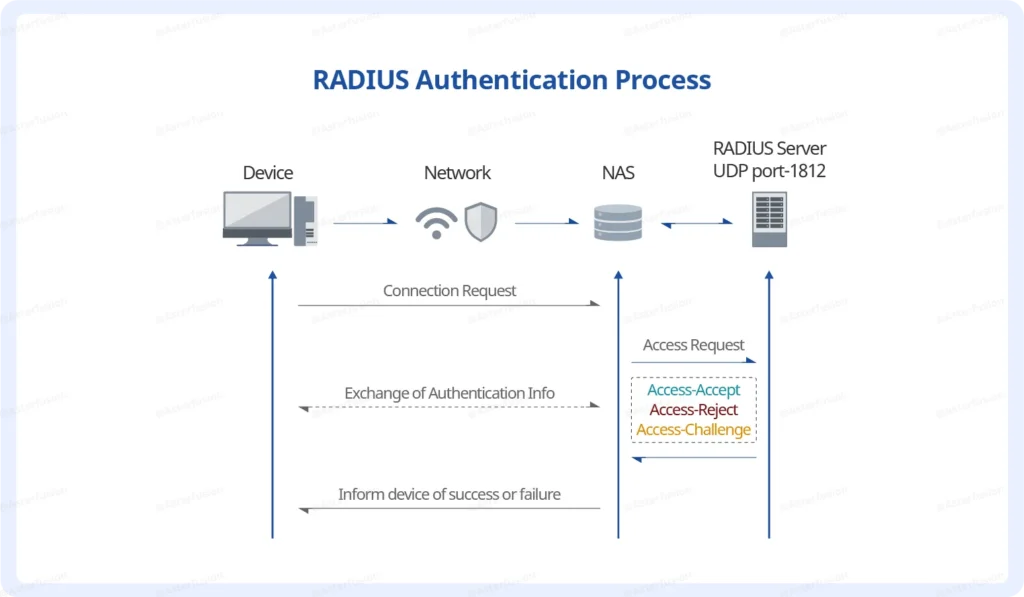
- User initiates a connection
A user connects to the network (e.g., via 802.1X, Wi-Fi, or VPN) and submits credentials like a username/password or certificate. - RADIUS client forwards the request
The switch or AP (RADIUS client) wraps the credentials into a RADIUS Access-Request and sends it to the RADIUS server via UDP (port 1812). - RADIUS server verifies credentials
It checks the credentials against a backend identity database (e.g., Active Directory, LDAP, local DB, etc.). - Server responds with decision
- Access-Accept: User is authenticated and granted access.
- Access-Reject: User is denied access.
- Access-Challenge: Server requests more info (e.g., second factor).
- Policy enforcement
The server may also return authorization attributes such as:- VLAN assignment
- Access Control Lists (ACLs)
- Bandwidth restrictions
- Accounting (optional)
If enabled, RADIUS accounting logs session details (start/stop time, data usage, etc.) to help with auditing and billing.
4. What is TACACS+ and How Does It Work?
TACACS+ (Terminal Access Controller Access-Control System Plus) is a network protocol developed by Cisco and widely used for controlling access to network devices such as routers, switches, and firewalls. It implements the AAA framework — Authentication, Authorization, and Accounting — to manage user access and activity in network environments.
TACACS+ follows a client-server model, with three main functions:
4.1. Authentication: Verifies the user’s identity:
- A user attempts to access a network device (e.g., via SSH or Telnet)
- The device acts as a TACACS+ client and sends an authentication request to the TACACS+ server
- The server checks the username/password (against a local DB, LDAP, etc.)
- If validated, access is granted; otherwise, access is denied
4.2. Authorization: Determines what the authenticated user is allowed to do:
- The client asks the TACACS+ server whether the user can perform a specific action (e.g.,
show running-config, enter configuration mode) - The server responds with an allow or deny decision based on policy
- The device enforces the permissions accordingly
4.3. Accounting: Tracks user activity:
- Records when a user logs in/out, what commands they execute, and session details
- Sends logs to the TACACS+ server for auditing and reporting
- Helps with troubleshooting, compliance, and security reviews
TACACS+ vs. RADIUS – Key Differences
| Feature | TACACS+ | RADIUS |
| Transport Protocol | TCP (port 49) | UDP (ports 1812/1813) |
| Encryption Scope | Entire payload | Password field only |
| AAA Separation | Yes (auth, authz, and accounting split) | No (mixed handling) |
| Authorization Detail | Granular (command-level control) | Basic (coarse access control) |
| Developer | Cisco | IETF |
| Common Use Cases | Cisco devices, high-security networks | General network access (e.g. 802.1X) |
5. What is MAB (MAC Authentication Bypass)?
MAB (MAC Authentication Bypass) is a network access authentication method that uses a device’s MAC address as its identity. It is typically used as a fallback when a device does not support 802.1X authentication. Instead of username and password, the switch uses the device’s MAC address to request authentication from an authentication server (usually a RADIUS server).
Key Features of MAB
- Designed for non-802.1X devices: Suitable for devices that cannot perform 802.1X, such as printers, IP phones, surveillance cameras, etc.
- No user interaction required: Devices connect automatically without entering credentials.
- Basic access control: Often combined with NAC (Network Access Control) policies.
- Lower security: MAC addresses can be easily spoofed, so MAB is less secure than 802.1X.

How MAB Works?
MAB is typically implemented on network switches or wireless controllers that support 802.1X, and works alongside a RADIUS server. The basic workflow is:
- Step 1: Port Initialization
When a device connects, the switch port is initially in an unauthorized state. - Step 2: 802.1X Attempt
The switch first attempts 802.1X authentication. If the device does not respond (i.e., does not support 802.1X), the switch falls back to MAB. - Step 3: MAC Address Learning
The switch learns the MAC address of the device and formats it as the username and password. - Step 4: RADIUS Request
The switch sends a RADIUS authentication request to the server, using the MAC address as credentials. - Step 5: Authentication Result
If the MAC address is listed and allowed on the server, access is granted, and the port becomes authorized.
MAB vs. 802.1X- Key Differences
| Feature | 802.1X | MAB |
|---|---|---|
| Authentication | Interactive (username/password, certificates) | Non-interactive (MAC address only) |
| Security | High (encrypted, identity-based) | Low (MAC spoofing is easy) |
| Supported Devices | Computers, smart devices | Printers, cameras, IP phones, etc. |
| Client Requirement | Needs 802.1X-capable supplicant | No supplicant needed |
Typical Use Cases for MAB
- Office printers, faxes, projectors
- Enterprise IP telephony systems
- Surveillance cameras and security devices
- Basic guest access on enterprise networks
Contrast of 802.1X/ EAP/TACACS+/RADIUS/MAB
| Feature / Protocol | 802.1X | TACACS+ | RADIUS | EAP | MAB |
|---|---|---|---|---|---|
| Type | Access Control Framework | Authentication Protocol | Authentication & Accounting Protocol | Authentication Framework | MAC-based Access Method |
| Purpose | Controls network port access | Centralized authentication for CLI access | Centralized auth for network access | Supports various authentication methods | Used when devices don’t support 802.1X |
| Works With | EAP, RADIUS | Routers, switches, firewalls (CLI access) | 802.1X, VPN, Wi-Fi, etc. | 802.1X, WPA2-Enterprise, VPN, etc. | Legacy or non-802.1X devices |
| Authentication Data | User credentials via EAP | Username/password or tokens | Username/password, certificate, etc. | Depends on EAP method used | MAC address |
| Encryption | Supports EAP-based encryption | Encrypts full payload | Encrypts only password field | Depends on method (EAP-TLS, PEAP, etc.) | No encryption (MAC address is visible) |
| User Interaction | Yes (802.1X supplicant required) | Yes (manual login for CLI) | Yes | Yes or no (depends on method) | No (automatic via MAC) |
| Security Level | High (with EAP-TLS, PEAP, etc.) | High | Medium to High (depends on setup) | Varies (EAP-TLS = very high, EAP-MD5 = low) | Low |
| Device Compatibility | Modern client devices with supplicant | Network devices (e.g., SSH/console auth) | Any RADIUS-compatible device | Any device supporting EAP | Legacy/IoT/non-802.1X devices |
| Common Use Case | Wi-Fi / Wired enterprise access | Admin login to network devices | Network access control & accounting | Wi-Fi, VPN, or wired port-based auth | IP phones, printers, cameras |
| Protocol Transport | Works over LAN (L2) with EAP & RADIUS | TCP (port 49) | UDP (ports 1812/1813) | Used inside 802.1X or over PPP | Used inside 802.1X as fallback |
How Should Enterprises Choose?
Strict Identity Verification for Endpoint Access: Choose: 802.1X + RADIUS + EAP
If you want every endpoint (PCs, employee smartphones) to authenticate before accessing the network, this is the most secure solution. Use 802.1X for network access control, with a RADIUS server handling identity verification. EAP (Extensible Authentication Protocol) serves as the authentication framework—e.g., using EAP-TLS for certificate-based authentication.
Ideal for: Medium to large enterprises, financial institutions, and government agencies where security is critical.
Devices That Don’t Support 802.1X?-Use MAB (MAC Authentication Bypass)
For legacy or lightweight devices like printers, IP cameras, or IoT endpoints that don’t support 802.1X, MAB can be used.MAB identifies devices by their MAC addresses, and RADIUS is used to assign access permissions. It’s recommended to deploy MAB together with 802.1X as a fallback method.
Need to Control Admin Access to Switches or Routers? Choose: TACACS+
TACACS+ is designed for authenticating and controlling administrator access to network devices like switches, routers, and firewalls. It supports granular command-level authorization, distinguishing between “read-only” and “config” roles, and provides audit logs of operations. It’s generally not used for endpoint access, but for securing the network management layer.
What About Small and Medium-Sized Enterprises (SMEs): RADIUS + MAB
If you’re not ready to implement a full certificate-based 802.1X system, you can start with RADIUS + MAB, and gradually move to full 802.1X deployment. For organizations with less stringent administrative control needs, local account management may suffice in the short term, with TACACS+ introduced as the network grows.
| Scenario | Recommended Solution | Use Case Details | Recommended For |
| Strict Identity Verification for Endpoint Access | 802.1X + RADIUS + EAP | PCs and employee smartphones must authenticate before accessing the network. EAP (e.g., EAP-TLS) handles certificate-based authentication. | Medium to large enterprises, financial institutions, government |
| Devices That Don’t Support 802.1X | MAB + RADIUS | Legacy or lightweight devices (printers, IP cameras, IoT) without 802.1X support use MAB for MAC-based authentication. | Environments with non-802.1X-capable devices |
| Admin Access to Network Devices | TACACS+ | Authenticate and control admin access to switches, routers, and firewalls. Enables command-level permissions and auditing. | IT departments managing infrastructure |
| Small and Medium-Sized Enterprises (SMEs) | RADIUS + MAB (start); TACACS+ (future) | Start with RADIUS + MAB to simplify deployment; use local accounts initially and adopt TACACS+ as network scales. | Small to medium enterprises starting network security deployment |



