Multicast IGMP Snooping in SONiC Enterprise Switches for Optimal Traffic
written by Asterfuison
Table of Contents
Introduction
Imagine this scenario: in an office, the finance department is holding an internal meeting via a video conferencing system. It’s a typical “multicast” situation — a single sender transmitting to multiple specific receivers. However, at the network level, a problem is occurring: the finance meeting video stream, like a loudspeaker, is being sent to the administrative, marketing, and even reception computers.
This is the core issue that Multicast IGMP Snooping in SONiC aims to address. So, who exactly benefits from its solution? And how does it resolve the problem elegantly?
Ⅰ. “Blind Flooding” Problem of Multicast Traffic
In traditional Layer 2 switching networks, if switches lack mechanisms to control multicast traffic, multicast frames are flooded across the entire broadcast domain. These frames are sent to all ports, regardless of whether a host on that port actually needs the data.
This flooding behavior causes unnecessary multicast traffic to reach unrelated ports, leading to network congestion. At the same time, switches must handle a large number of redundant forwarding operations, which increases their processing load. Not only do switches experience higher utilization, but non-member endpoints also receive unwanted multicast data—raising CPU usage and application overhead on those devices.
In other words, without a mechanism to identify which hosts truly need the data, the advantages of multicast can turn into a burden. The problem to solve here is clear: reducing the complexity faced by network administrators and operations teams when managing multicast traffic at Layer 2.
Ⅱ. How Multicast IGMP Snooping in SONiC Works
IGMP Snooping is a multicast management technique implemented on Layer 2 switches, based on the Internet Group Management Protocol (IGMP) defined by the IETF. Its logic is straightforward: by “snooping” on IGMP messages exchanged between hosts and Layer 3 devices (such as routers), the switch builds a multicast address-to-port mapping table. This allows multicast data to be forwarded only to the ports that have requested it, instead of flooding it across the entire broadcast domain.
To understand how Multicast IGMP Snooping in SONiC works in detail, it’s important to first review the following concepts.
1. IGMP Message Types
Through IGMP Snooping, a Layer 2 switch monitors several key types of IGMP messages to manage multicast traffic efficiently:
- General Query – Sent by the IGMP querier to discover which hosts within the broadcast domain are interested in receiving multicast data.
- Membership Report – Sent by a host to indicate its intention to join a specific multicast group.
- Leave Group – Sent by a host to notify that it no longer wishes to receive traffic for a particular multicast group.
- Group-Specific Query – Sent by the querier after receiving a Leave Group message to verify whether other members on the network are still subscribed to that multicast group.
By analyzing these messages, the switch dynamically updates its Multicast Forwarding Table (MFT) at Layer 2, ensuring multicast traffic is delivered only to the ports that have active subscribers.
2. Building the Forwarding Table and Handling Multicast Traffic
IGMP Snooping maintains a Layer 2 MFT on the switch. This table records the mapping between switch ports and multicast group addresses. When the switch detects an IGMP Membership Report, it learns which ports have hosts that have subscribed to specific multicast groups.
With the MFT in place, multicast traffic can be forwarded precisely rather than flooded. When a multicast frame arrives at the switch, the forwarding process follows this logic:
The switch checks the I/G bit (Individual/Group bit) in the destination MAC address.
- If it’s a multicast frame, the switch looks up the destination in the MFT.
- If a match is found: Forward only to the subscribed ports.
- If no match is found: Optionally flood the frame, depending on configuration.
- If it’s not a multicast frame: the switch handles it using normal Layer 2 unicast forwarding rules.
Through this mechanism, multicast traffic is transformed from a “flood-to-all-ports” behavior to a targeted delivery model, significantly improving network efficiency and reducing unnecessary load on both switches and end hosts.
3. IGMP Snooping Proxy and Querier
IGMP Snooping supports additional operating modes that enhance multicast management in different network environments.
- IGMP Snooping Proxy In some networks, a switch can operate as an IGMP proxy. In this mode, the switch aggregates join and leave messages from downstream hosts and reports them to the upstream router or querier. This approach helps reduce IGMP control traffic and optimizes multicast signaling efficiency.
- IGMP Querier vs. IGMP Snooping Querier
- IGMP Querier: Typically, an IGMP Querier is a Layer 3 device (such as a multicast router) responsible for sending IGMP Query messages. It establishes and maintains multicast routing tables at the network layer, enabling proper multicast forwarding across Layer 3 boundaries.
- IGMP Snooping Querier: In pure Layer 2 or static IGMP environments without a Layer 3 device, a switch can act as an IGMP Snooping Querier. Functionally, it behaves similarly to a standard IGMP Querier by sending periodic IGMP Query messages to trigger hosts to respond with Membership Reports. These reports allow the switch to update its MFT. However, unlike a Layer 3 IGMP Querier, the IGMP Snooping Querier only affects the Layer 2 forwarding state — it does not maintain or modify Layer 3 multicast routing tables.
The following table summarizes the differences between the two types of forwarding tables:
| Querier Type | Core Function | Forwarding Table Layer | Table Maintainer | Table Contents | Update Mechanism |
| IGMP Snooping Querier | Simulates a Querier by sending IGMP Query messages to trigger Membership Reports and update the MFT | Layer 2 – Multicast Forwarding Table (MFT) | Layer 2 Switch (IGMP Snooping) | Port ↔ Multicast MAC Address | Listens to Membership Report / Leave / Query messages |
| IGMP Querier | Periodically sends IGMP Query messages and maintains the Layer 3 multicast routing table, enabling inter-VLAN or inter-subnet multicast forwarding | Layer 3 – Multicast Routing Table | Layer 3 Device (IGMP Querier or Multicast Router) | Multicast IP Address ↔ Next-Hop Interface | IGMP Query messages + Multicast Routing Protocols |
In other words, the Querier is responsible for asking the questions, while Snooping is responsible for recording the answers. Together, they maintain the MFT to enable precise and efficient multicast forwarding.
Ⅲ. Benefits of Multicast IGMP Snooping in SONiC
With Multicast IGMP Snooping in SONiC, network administrators and operations teams can significantly reduce unnecessary Layer 2 multicast flooding. The technology delivers several key benefits:
- Improved Network Efficiency Multicast traffic is forwarded only to the ports that actually need it. This minimizes bandwidth consumption and reduces buffer pressure on switches—eliminating frequent bandwidth-related alerts.
- Optimized Device Performance By preventing switches and endpoints from processing irrelevant multicast packets, overall system performance and network stability are improved.
- Enhanced Manageability The MFT is dynamically maintained by the switch, requiring no manual configuration on individual ports. This makes multicast management far more scalable across large enterprise networks.
- Broad Deployment Flexibility IGMP Snooping is applicable in a wide range of environments, including enterprise campuses, educational networks, and data centers. It provides particular benefits in multicast-intensive scenarios such as IPTV, video surveillance, and real-time data distribution.
- Automation and Fault Tolerance The MFT is built and updated automatically. When hosts join or leave multicast groups, the table is refreshed in real time. Combined with IGMP Querier and Proxy functions, this enables fast adaptation to topology changes.
Ultimately, these improvements translate into lower operational costs and more reliable services. Without Multicast IGMP Snooping in SONiC, networks often compensate for multicast flooding by upgrading to higher-bandwidth switches or increasing link capacity—an explicit cost. Meanwhile, business interruptions caused by congestion, such as slow customer service or disrupted training sessions, represent a hidden cost.
By implementing IGMP Snooping, organizations can avoid redundant hardware expansion and ensure that critical applications—such as CRM systems or video conferencing—operate smoothly without multicast-induced congestion. The result is improved operational efficiency and a more stable user experience.
Ⅳ. How IGMP Snooping Works in Practice
Typical use cases for multicast include video conferencing, live streaming, and IPTV.
In the Asterfusion CX-M series switches, IGMP Snooping and related multicast management features are supported to enable efficient multicast traffic handling in these scenarios.
Let’s explore how Multicast IGMP Snooping in SONiC works through two typical network setups.
1. Layer 3 Network Topology
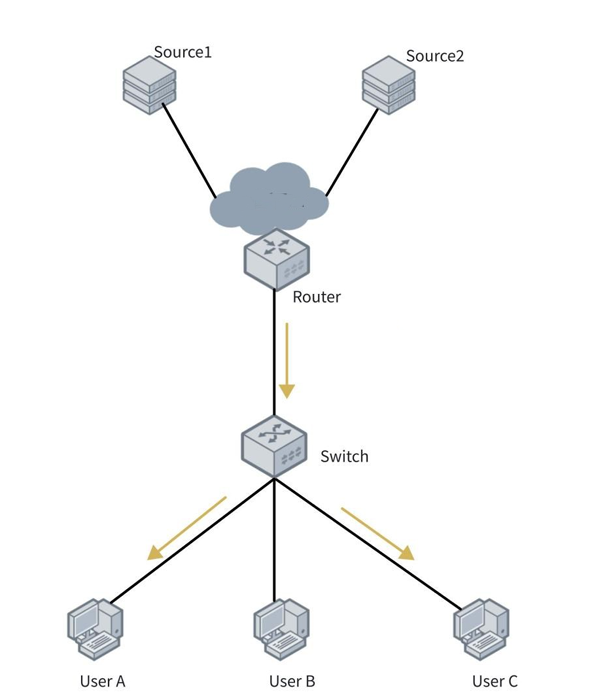
In this network, multiple multicast sources (e.g., Source1 and Source2) provide multicast video services with group address 224.1.1.1. Some LAN users (such as User A and User C) want to receive this video stream via multicast.
Configuration approach:
- Enable PIM and IGMP on the Layer 3 router to route multicast traffic into the user subnet.
- Enable IGMP Snooping on the Layer 2 switch so it can build and maintain the MFT, ensuring multicast traffic is only sent to interested users—preventing unnecessary flooding and potential security risks.
- Enable IGMP Snooping Proxy on the switch to reduce IGMP signaling load on the router.
Workflow:
- Join:User A and User C send IGMP Membership Reports to join group 224.1.1.1.
- MFT creation: The switch receives the reports and creates Layer 2 MFT entries, mapping 224.1.1.1 to the corresponding ports. With IGMP Snooping Proxy enabled, the switch forwards a aggregated Membership Report to the router.
- Layer 3 table update: The router receives the report, updates its Layer 3 multicast routing table, and forwards multicast traffic to the switch.
- Multicast forwarding: The switch forwards multicast packets to User A and User C based on the MFT.
- Query mechanism: The router, acting as the IGMP Querier, periodically sends General Query messages. When the switch receives a query, if operating in IGMP Snooping Proxy mode, it sends IGMP Query messages to all non-receiving ports (i.e., ports other than the ingress port) and reports the results back to the router.
2. Layer 2 Network Topology
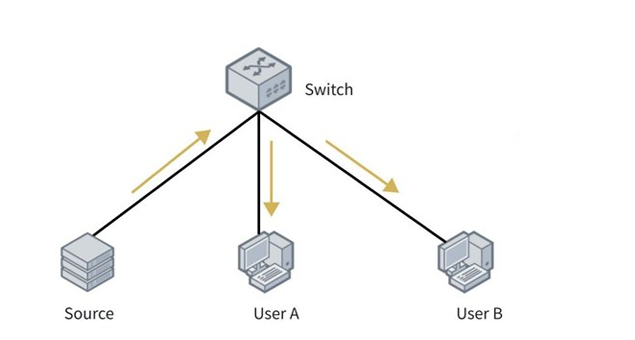
As shown in the diagram, within a pure Layer 2 network environment without Layer 3 devices, the multicast source, User A, and User B reside in the same VLAN. The multicast source sends multicast data to the multicast group 224.1.1.1. User A, acting as a multicast receiver, joins the multicast group 224.1.1.1 using IGMPv2, with the goal of achieving precise multicast data transmission in the Layer 2 network via IGMP Snooping.
Configuration Approach:
- Enable the IGMP Snooping function on the Switch.
- Enable the IGMP Snooping querier function.
Workflow:
- Multicast traffic with the destination address 224.1.1.1 is sent from the Source to the Switch. Since no valid Layer 2 multicast forwarding entry can be found, the Switch discards the multicast traffic.
- User A sends an IGMP membership report message to join the multicast group 224.1.1.1.
- After receiving the membership report message, the Switch establishes a Layer 2 multicast forwarding entry. Subsequently, it forwards the multicast traffic (originating from the Source and destined for 224.1.1.1) to User A.
- The Switch periodically sends general query messages. Upon receiving these general query messages, User A sends IGMP membership report messages to maintain the Switch’s Layer 2 multicast forwarding entry.
Ⅴ. Conclusion
In essence, the core logic of Multicast IGMP Snooping in SONiC lies in “on-demand allocation”: it addresses the pain point of “blind broadcasting of multicast traffic”. Through a simple “listening – table establishment – forwarding” mechanism, data is only delivered to where it is needed. For operation and maintenance personnel, it reduces management troubles; for enterprises, it cuts costs and ensures business operations; for users, it enhances the internet experience.
If there are multicast scenarios in your campus network (such as video conferences, live broadcasts, and surveillance), IGMP Snooping is indispensable. The Asterfusion CX-M switch can meet your needs.
For more details, contact us !





