Open Networking Solution by Campus: Powered by End-to-End BGP EVPN & OpenWiFi(Ⅱ)
written by Asterfuison
This article continues to explore Asterfusion’s open campus network architecture, focusing on overlay networks and highlighting some of their advanced features, and robust network security solutions.
Asterfusion Overlay Networks for Scalable and Secure Layer 2/3 Connectivity
Understanding the Challenges of Layer 2 Networks
Through discussions with campus network clients, Asterfusion identified several benefits of Layer 2 networks, such as allowing endpoints to connect to firewalls, transparently access DHCP servers, and supporting essential LAN protocols (e.g., printing, file sharing, and screen sharing). However, as networks scale, Layer 2 networks face significant challenges related to stability and scalability, which often lead to increased costs.
To address these issues, the traditional approach has been to segment large networks into smaller Layer 2 networks, each serving hundreds or thousands of endpoints. However, this method introduces drawbacks when scaling in large deployments, such as inefficiency and complexity.
So, is there a way to preserve the convenience of Layer 2 networks while improving scalability?
Leveraging EVPN for Scalable and Stable Layer 2 Networks
Asterfusion’s answer lies in EVPN (Ethernet VPN) technology. By utilizing EVPN, Layer 2 extensions become more scalable, leveraging protocols like BGP and OSPF to enhance network stability. Combining overlay technologies such as VXLAN and EVPN enables Asterfusion to create flexible, scalable Layer 2 overlays. Advanced technologies like VPWS, Etree, and E-LAN further boost network agility and scalability.

Achieving End-to-End Endpoint Isolation
One common security concern with traditional Layer 2 networks is ensuring endpoint isolation. In a typical Layer 2 setup, it is essential to prevent unauthorized communication between endpoints. But how can we ensure this level of isolation?
Asterfusion’s solution involves implementing port isolation on leaf switches and applying EVPN horizontal segmentation on border leaf switches to block direct communication between endpoints. Additionally, on access points (APs), strict forwarding rules are enforced to prevent wireless endpoints from communicating directly with each other. All traffic from these endpoints must pass through a firewall before interacting with other devices, ensuring that security policies are consistently enforced across the network.

Dynamic Endpoint Access and VLAN Configuration
Connecting endpoints to a Layer 2 VPN requires effective dynamic integration methods. Asterfusion employs four key technologies to achieve this:
- Port-based service interface
- VLAN-aware bundling
- VLAN-based service IDs
- Dynamic VLAN assignment
These technologies ensure efficient and dynamic integration of endpoints into the network, facilitating seamless user experiences and robust network performance.
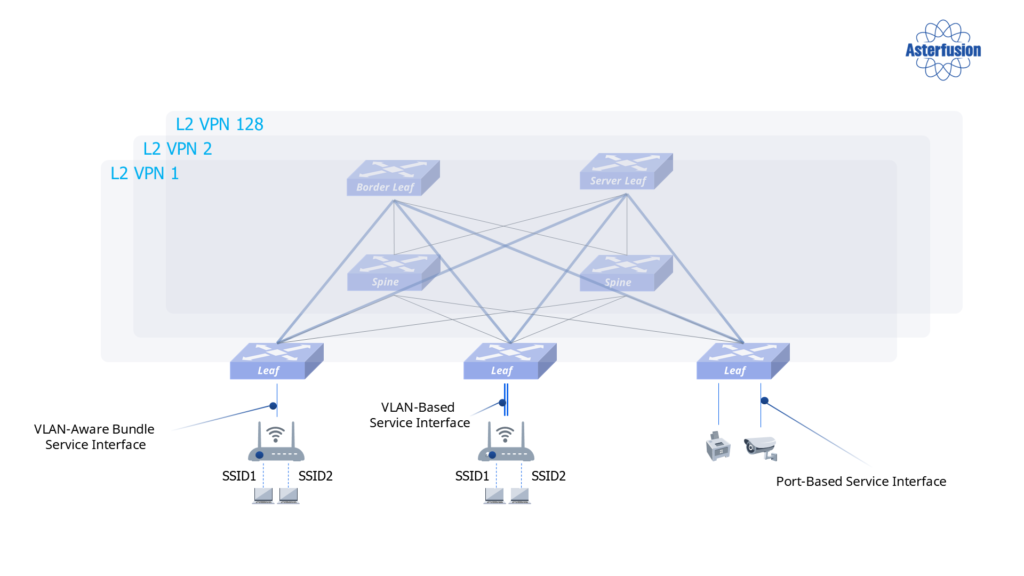
By combining these approaches, Asterfusion delivers a network architecture that balances the convenience of Layer 2 connectivity with the scalability and security required for modern campus networks.
How Asterfusion Solving Layer 2 Broadcast Challenges?
Anyone in networking knows the frustration of dealing with broadcast storms in Layer 2 networks. They consume bandwidth, block normal traffic, and overload devices, leading to delays, packet loss, and even complete network disruption. In extreme cases, they can crash devices or trigger reboots. And the risks don’t end there—broadcast storms open the door for security vulnerabilities, leaving your network exposed to sniffing and attacks that can jeopardize both stability and security.

But with Asterfusion’s three-layer network architecture, you can finally put an end to this nightmare. Here’s how we tackle it:
- AP Forwarding: Strict rules ensure all traffic is directed straight to the leaf switches, eliminating unnecessary detours.
- Leaf Switch Traffic Management: Most broadcast traffic is discarded, while only essential traffic (like ARP and DHCP) is proxied and forwarded as unicast.
- BGP Control: BGP ensures there are no loops, keeping broadcast issues in check.
- ARP Suppression: Techniques are applied to minimize broadcast traffic when downlinking to other leaf switches.
- Unicast Conversion: Once traffic reaches the AP, broadcasts are converted to unicast, effectively reducing security risks and optimizing resource usage in the wireless domain.
With this approach, Asterfusion ensures your network stays fast, secure, and efficient, even in complex environments.
Enhancing Device Discovery and Network Efficiency with EVPN and VXLAN
In traditional Local Area Network (LAN) environments, multicast protocols such as MDNS, SSDP, and LLMNR are commonly used for device discovery. These protocols allow clients to automatically locate and connect to devices like printers, projectors, and other networked equipment within the same Layer 2 (L2) network, without requiring manual IP address configuration. This capability is especially useful in small-scale networks, where it simplifies user operations and improves device connectivity efficiency.
However, there are inherent limitations to this approach. Multicast traffic is typically confined to a single L2 broadcast domain (e.g., a VLAN), meaning it cannot easily traverse network boundaries. As networks grow and become more complex, this limitation can become a significant bottleneck.
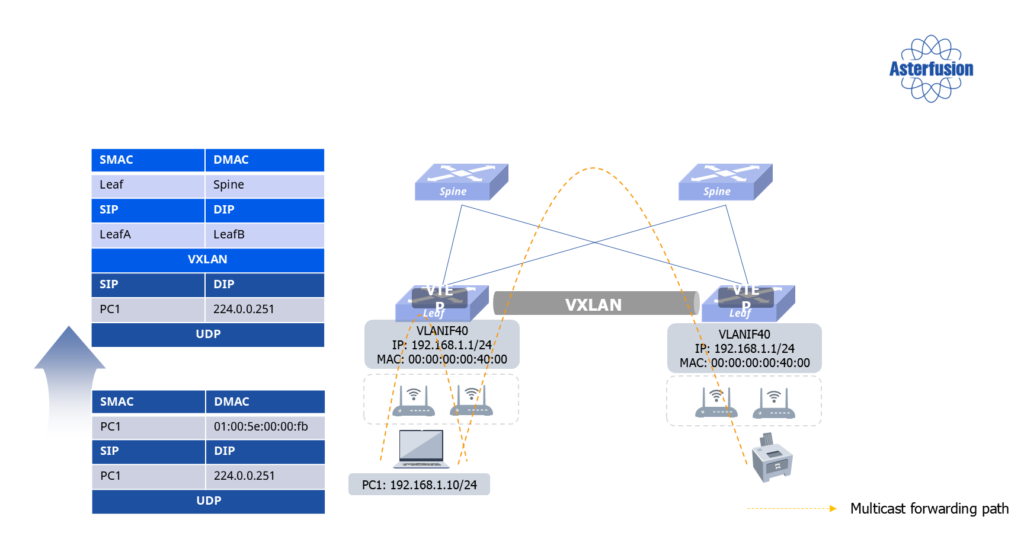
To overcome this challenge, Asterfusion leverages a combination of EVPN and VXLAN. EVPN provides a BGP-based control plane, while VXLAN enables efficient cross-network transmission by encapsulating multicast traffic. Here’s how it works: Leaf switches identify multicast traffic, encapsulate it into VXLAN packets, and forward these packets through tunnels to target leaf switches. These target switches then decapsulate the traffic and distribute it within their local networks. This process effectively enables device discovery across different network domains.
This solution eliminates the constraints of traditional multicast, enabling flexible and efficient device discovery across modern campus networks. It also improves network scalability and resource utilization, making it ideal for expanding and evolving network infrastructures.
Network Security Measures
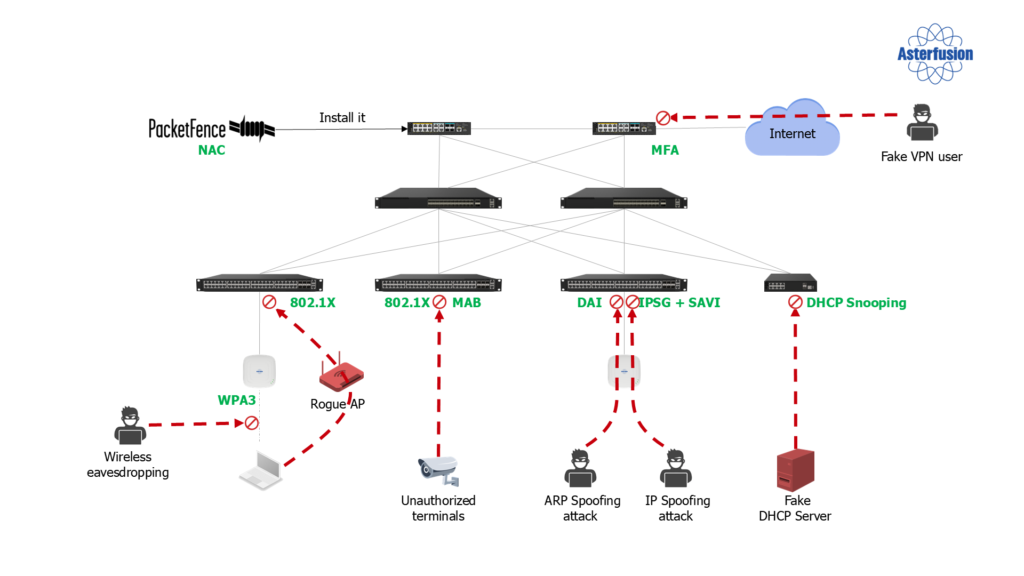
Enterprise and campus networks are susceptible to security risks such as wireless eavesdropping, rogue Access Points (APs), and unauthorized devices. These threats not only disrupt normal network operations but can also lead to significant security and financial losses for businesses. Therefore, ensuring the security of wireless networks is crucial for protecting enterprise assets. To address these security challenges, our network architecture incorporates several robust security measures. Below, we highlight some of the key security features:
- Authentication: We use WPA3, 802.1X, MAB, and other methods to ensure that only authorized devices can access the network.
- Attack Prevention: Through technologies like DII (Dynamic IP Inspection), IP and MAC binding, and DHCP snooping, we defend against ARP spoofing and IP impersonation.
- Protecting Against Rogue DHCP Servers: A DHCP response mechanism ensures that only legitimate DHCP servers can provide services.
- Remote Access Security: We enhance remote access security using multi-factor authentication (MFA) and NAC (Network Access Control) servers.
How Dynamic VLAN Technology Enhances Network Operations
Optimized VLAN Management for Seamless VPN Access
To optimize user access to various VPNs, we utilize Dynamic VLAN technology. This solution enables users to be dynamically assigned to specific VPNs based on their authentication credentials. By centralizing configuration on the RADIUS server, we eliminate the complexity of static setups, reducing the potential for configuration errors. The RADIUS server manages all security and access policies, dynamically assigning VLANs based on user credentials. This approach not only improves VPN access efficiency but also supports seamless roaming and lightens the administrative workload for network administrators.

Seamless Roaming with Dynamic VLAN Support
The power of Dynamic VLAN becomes evident when users roam across different access points (APs).
For example, when a user connects to a VLAN through the RADIUS server in a conference room, and later switches to another AP upon leaving the room, the system ensures that the user’s original IP address and VLAN remain consistent during the roaming process. This continuity is achieved through the seamless interaction between the RADIUS server and the leaf switches, which simplifies the roaming process and enhances the overall user experience.

In the next article, we’ll dive into the powerful Asterfusion OpenWiFi-compatible controller, designed to streamline the management and monitoring of entire campus networks. By offering centralized control, it simplifies both user experience and network management. Join us as we explore its standout features and discover how it empowers campus networks to operate more efficiently and securely.



