Table of Contents
To understand Dynamic VLAN thoroughly, it is essential to first grasp what VLAN and static VLAN are.
A VLAN (Virtual Local Area Network) is a Layer 2 technology for isolating broadcast domains, confining broadcast traffic within its boundaries. Consider each VLAN as a dedicated enclosed corridor:
- Devices in the VLAN exchange broadcast traffic only within this space.
- Broadcast frames can’t enter other VLANs without Layer 3 routing.
This mitigates broadcast storms and enables network isolation, boosting security and efficiency.
Static VLAN is configured manually: an administrator assigns a VLAN to a switch port, and this mapping remains unless the configuration is changed. Static VLAN enforces persistent port-based VLAN mappings.
Now let’s turn to Dynamic VLAN.
I. What is Dynamic VLAN ?
1. What is it ?
With evolving network demands, static VLAN can no longer meet requirements, giving rise to Dynamic VLAN.
Dynamic VLAN automatically assigns and reassigns devices to VLANs based on predefined criteria. Unlike static VLAN that relies on fixed port-to-VLAN mappings, Dynamic VLAN adapts dynamically to network changes. For example, a device’s VLAN membership can shift automatically based on factors like its MAC address, authenticated user, or IP address.
Many readers struggle to distinguish between Static and Dynamic VLANs. Below is a comparison for your reference, should you need it.
2. Comparison between Static and Dynamic VLAN
| Feature | Static VLAN | Dynamic VLAN |
| Configuration | Manual port assignment | Automatic assignment via policies |
| Flexibility | Low (changes require reconfiguration) | High (adapts to device/user) |
| Security | Moderate (fixed assignments) | Higher (based on authentication) |
| Management | Simple but rigid | Complex but scalable |
Ⅱ. Why Do We Need Dynamic VLAN ?
- BYOD (Bring Your Own Device):
Employees and guests use their own laptops, phones or other devices that require different network access. - Security Compliance:
Ensure devices are placed in the appropriate VLANs based on predefined policies. - Simplified Management:
Avoid manual reconfiguration when network requirements change. - Guest Networking:
Automatically assign guests to an isolated VLAN without administrator configuration.
Ⅲ. How Does Dynamic VLAN Work ?
Dynamic VLAN relies on an authentication and policy assignment mechanism between the device (a switch or an AP) and an external policy server (often RADIUS).
There are three common implementation approaches.
1. VMPS (VLAN Membership Policy Server)
This is a Cisco proprietary method where the switch queries a VMPS server with the device’s MAC address to determine VLAN assignment.
This method is no longer in use and is provided here for reference only
2. MAC Authentication Bypass (MAB)
For devices that do not support 802.1X authentication (e.g., IP phones, printers), MAB is suitable. For such devices, MAB is ideal: the switch uses the device’s MAC address as the authentication credential and queries a RADIUS server for VLAN assignment, making it useful when 802.1X is unavailable.
3. 802.1X + RADIUS (Industry Standard)
This is a preferred modern approach.
- The switch forwards authentication requests to a RADIUS server.
- Based on the credentials (username/password, certificate, etc.), the RADIUS server sends back VLAN assignment attributes.
- VLAN changes happen automatically, without manual switch port configuration.
Let’s explore how a RADIUS server cooperates with a switch in an 802.1X and RADIUS environment.
1. Trigger Conditions
Dynamic VLAN assignment is typically triggered by:
- Device network access (wired switch port or wireless AP association)
- Authentication requests (802.1X, MAC authentication, WebAuth, etc.)
- Policy matching (RADIUS server returns VLAN based on device/user attributes)
2. Core Components of Dynamic VLAN
| Component | Role |
| Client Device | Endpoints initiating connections (PCs, phones, IoT devices) |
| Switch/AP | Enforces port/VLAN assignment; forwards authentication requests |
| RADIUS Server | Validates credentials and returns VLAN attributes (e.g., Cisco ISE, FreeRADIUS) |
| Policy Database | Stores VLAN mapping rules (e.g., user group→VLAN, device type→VLAN), typically hosted on the RADIUS server |
3. Workflow of Dynamic VLAN
Let’s take the picture below as a reference.
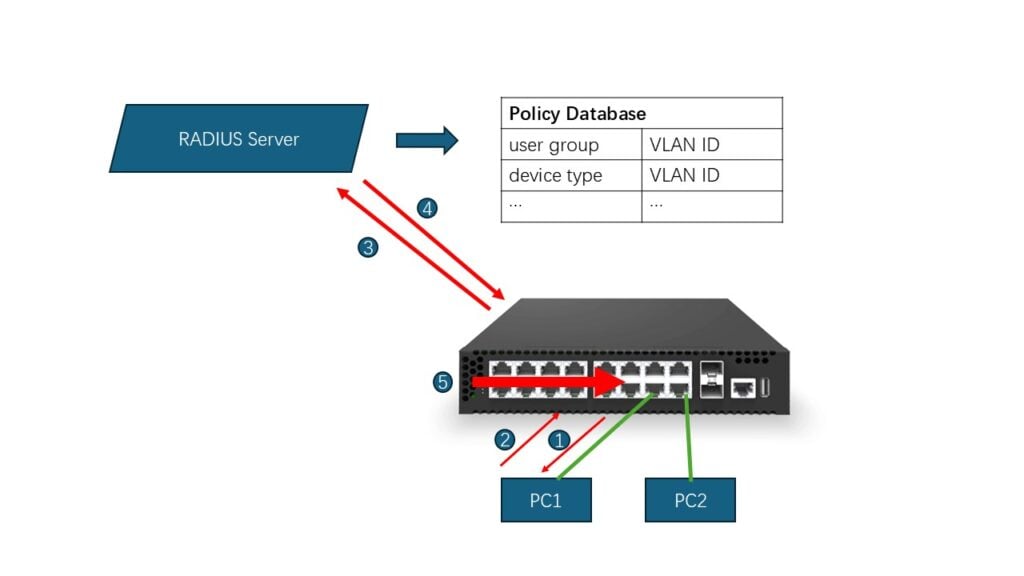
Step 1: Device Network Connection
Devices connect via wired (switch port) or wireless (AP SSID).
Switch/AP detects link activation and initiates authentication.
Step 2: Authentication Request (EAPOL)
Switch/AP sends EAPOL frames to client devices to request authentication, then device responds with credentials (e.g., certificates, username/password).
Step 3: RADIUS Interaction (802.1x core mechanism)
The switch/AP encapsulates authentication data (such as credentials submitted by the endpoint) into a RADIUS Access-Request packet and sends it to the RADIUS server.
Upon receiving the requests, the RADIUS server compares and evaluates the authentication information in the packet (user identity, device MAC, etc.) against its stored policy rules (e.g. user identity, device MAC address, time/location restrictions), and ultimately decides whether to approve the authentication and return the corresponding VLAN assignment information.
Note: If pre-shared key (PSK) + 802.1X hybrid authentication is enabled, the AP must first verify the PSK for the wireless connection before initiating 802.1X user authentication.
Step 4: VLAN Assignment
If approved, RADIUS returns Access-Accept packet with VLAN attributes.
Step 5: Switch Enforcement
Switches directly assign physical ports to the specified VLAN, and terminal data frames are transmitted with native VLAN tags.
APs associate wireless sessions (e.g., SSIDs, authenticated clients) with specified VLANs, with wireless terminal frames carrying assigned VLAN tags.
Step 6: Session Maintenance
Reauthentication intervals can be optionally set manually (e.g., every 4 hours).
Fallback to default VLAN on session termination.
Ⅳ. Where Is Dynamic VLAN Used ?
Dynamic VLAN is mainly implemented on:
* Managed switches (Layer 2 or Layer 3) that support 802.1X and RADIUS
* Wireless Access Points (APs) — often through dynamic SSID-to-VLAN mapping
* Campus and enterprise networks where user mobility and policy-based access control are required
Ⅴ. Dynamic VLAN Configuration Overview and Optimizations on Asterfusion OpenWiFi AP
In Wireless Scenario, Asterfusion has implemented optimizations and enhancements based on the OpenWiFi architecture. Through MAC authentication auto-recognition and access policy caching synchronization, terminals can seamlessly roam across the campus network after initial authentication—no repeated logins required—while retaining consistent VLAN IDs. This enables true “authenticate once, roam everywhere” connectivity.
If you want to know how to configure step by step based on OpenWiFi, please click here:
Dynamic VLAN Authorization Policy Application
If you want to know more about the mechanisms, you can refer to the documents below on the RFC website:
RFC 4675: RADIUS Attributes for Virtual LAN and Priority Support



